FAQ on Zoom Security Issues
FAQ
Since publishing report on Zoom security issues, there have been a wide range of responses to our research from the media, public, and Zoom itself. This document provides answers to frequently asked questions and addresses some inaccurate framings of our research.
On April 3, 2020, the Citizen Lab published a report on a technical analysis of the confidentiality of communications on the popular video chat application Zoom. On April 8, we released a followup report with details of a security vulnerability in Zoom’s waiting Room feature.
Since the publication of our report, there has been a wide range of responses to our research from the media, public, and Zoom itself. This document provides answers to frequently asked questions and addresses some inaccurate framings of our research.
What are the security issues your research found?
In our report published on April 3, we found that Zoom uses non-industry-standard encryption for securing meetings, and that there are discrepancies between security claims in Zoom documentation and how the platform actually works.
Zoom documentation claims that the app uses “AES-256” encryption for meetings where possible. However, in our testing, a single AES-128 key was used in ECB mode by all meeting participants to encrypt and decrypt audio and video. The use of ECB mode is not recommended because patterns present in the plaintext are preserved during encryption. What this finding means is that the encryption in Zoom does not seem to have been well-designed or implemented.
The AES-128 keys, which we verified were sufficient to decrypt Zoom packets intercepted in Internet traffic, appeared to be generated by Zoom servers, and in some cases, were delivered to participants in a Zoom meeting through servers in China, even when all meeting participants, and the Zoom subscriber’s company, were outside of China. This finding is significant because Zoom is a company that primarily serves customers in North America and sending encryption keys via servers in China may potentially open Zoom up to requests from authorities in China to disclose the encryption keys. While this scenario is plausible, we do not have evidence that authorities in China or any other state have actually obtained meeting encryption keys.
What is the security issue with the Zoom waiting room feature? Are they now safe to use?
In our report published on April 3, we noted that we found a security issue with Zoom’s waiting room feature. We did not publicize full details of the issue in our initial report because we believed that doing so might put user privacy at risk, and it seemed that Zoom would be able to appropriately address the issue in a short timeframe. This type of disclosure process is relatively standard in the information security field.
On April 7, Zoom reported to us that they had fixed the issue, and on April 8, Zoom’s CEO mentioned that the vulnerability had been fixed. We subsequently released a research note with details about the security vulnerability.
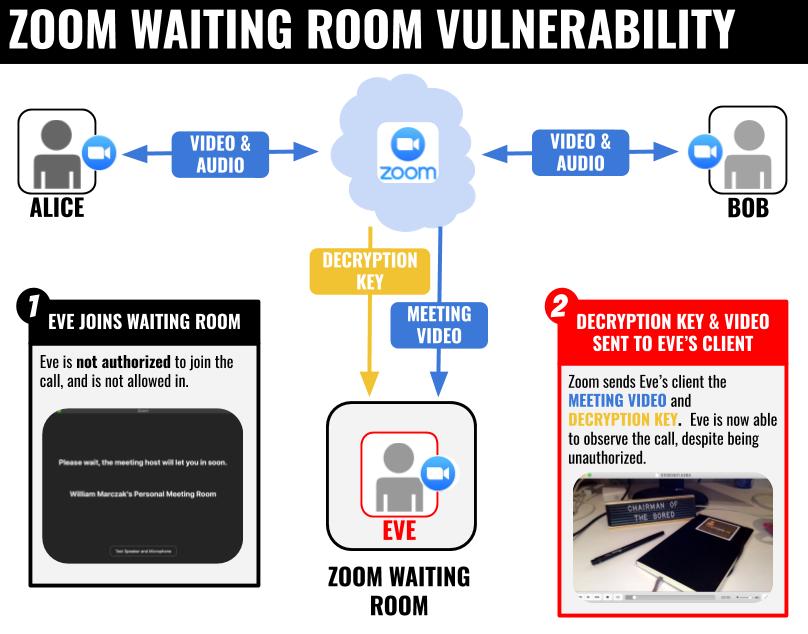
The issue we found is that Zoom servers provided both the encryption keys and a live video stream of the Zoom meeting to all users in the meeting’s waiting room, even if the waiting users had not been approved to join the meeting. This issue would enable an arbitrary, unauthorized Zoom user in a waiting Room to intercept and decrypt the “encrypted” video content. Figure 1 below provides an overview of the (now-fixed) vulnerability.
Is Zoom appropriate for confidential communications?
Based on the findings of our April 3 report, we discourage the use of Zoom in cases where strong confidentiality and privacy is required, including:
-
- Governments worried about espionage
- Businesses concerned about cybercrime and industrial espionage
- Healthcare providers handling sensitive patient information
- Activists, lawyers, and journalists working on sensitive topics
We should note that we have only tested the mainline Zoom app. We have not tested Zoom’s HIPAA/PIPEDA-compliant healthcare plan, or the ZoomGov software that is used by some US Federal Government agencies, so we are unaware if these versions have similar issues.
Is it safe to use Zoom for semi-public / public activities like taking a course or keeping in touch with friends and family?
If you are using Zoom for an activity that you may otherwise hold in a public or semi-public place (like participating in a course lecture, listening to a musical performance, or keeping in touch with friends and family), then our research findings should not necessarily be concerning.
Some ministries of education (e.g., Taiwan) and public school boards (e.g., New York) have made the decision to ban Zoom due to security and privacy considerations. The decision of what tools to use for institutional communications have to weigh a range of risks and requirements. However, based on our research, we do not see the need to ban Zoom for use cases not requiring robust confidentiality measures.
Zoom for Healthcare and Zoom for Government are currently being used in many jurisdictions. Do Citizen Lab findings address these Zoom products?
We have not tested Zoom’s HIPAA/PIPEDA-compliant healthcare plan, or the ZoomGov software that is used by some US Federal Government agencies. This is an area that would require additional analysis.
Is the Chinese government using Zoom to spy on users?
Charlie Kirk (founder of Turning Point USA) cited our report to support his claim that the “Chinese Communist Party is using Zoom as a way to spy on our citizens.” Our research does not provide support for this claim. While our research findings show that a well resourced actor like a nation state (including China) could leverage the security issues we found to target communications on Zoom, our methodology cannot produce a finding one way or the other about whether this surveillance is actually occurring. Politifact provides further details about Kirk’s claim.
What has Zoom done in response to these research findings?
In response to our research and concerns raised by other parties, Zoom has taken a number of actions regarding security.
Zoom has committed to a 90-day process to identify and fix security issues, including a third-party security review, enhancing their bug bounty program and preparing a transparency report.
In direct response to our research Zoom acknowledged the concerns we raised about their use of non-industry standard encryption and committed to making improvements, including the implementation of end-to-end encryption. Zoom also acknowledged that some Zoom users based outside of China would have connected to data centres within China, and indicated they had immediately put in place measures to prevent that from happening.
On April 8 2020, Zoom released a new version of their client that added additional security features. Zoom CEO Eric Yuan indicated in a video webinar that this new version fixed the waiting room security issue we identified. He also announced that Zoom had established a CISO Council and Advisory Board to assist with their privacy and security practices, and had hired former Facebook Chief Security Officer Alex Stamos as an advisor.
Can you recommend a secure video conferencing software?
The COVID-19 pandemic has made video and chat applications vital lifelines for governments, businesses, schools, and families around the world. Deciding what application is appropriate for you and what level of security you need for your use is a personal decision that must weigh your specific requirements and risks carefully. As the Electronic Frontier Foundation explains “There is no such thing as a perfect or one-size-fits-all messaging app. For users, a messenger that is reasonable for one person could be dangerous for another.” That said, for users that require secure communications, we advise choosing a tool with end-to-end encryption that has been validated as safe by independent research.
Our Security Planner web tool provides research-based security recommendations that are beneficial for a general population of users, most of the time.
The Electronic Frontier Foundation also provides further information on how to keep your communications secure in their Surveillance Self Defense Guide.