
By Whose Authority? Pegasus Targeting of Russian & Belarusian-Speaking Opposition Activists and Independent Media in Europe
In a joint investigation with Access Now, we found that seven Russian and Belarusian-speaking independent journalists and opposition activists based in Europe were targeted and/or infected with NSO Group’s Pegasus mercenary spyware.
Summary
- In a joint investigation with Access Now, we found that seven Russian and Belarusian-speaking independent journalists and opposition activists based in Europe were targeted and/or infected with NSO Group’s Pegasus mercenary spyware.
- This investigation describes hacking that took place between August 2020 and January 2023.
- Our findings also surfaced forensic artifacts that suggest (but do not prove) the possibility that at least five of the cases may be the result of targeting by a single NSO Group customer.
Click here to read the full report by Access Now.
Threats Against Russian and Belarusian-Speaking Opposition and Independent Media
In September 2023, we published a joint investigation with Access Now into the hacking of exiled Russian journalist Galina Timchenko with Pegasus mercenary spyware. Timchenko is the CEO and publisher of Meduza, a widely-respected Russian independent media group operating in exile. After this publication, in collaboration with Access Now and independent digital security expert Nikolai Kvantiliani, we expanded the investigation into the possible targeting of Russian and Belarusian-speaking independent media and political opposition.
Seven New Cases
The latest investigation identifies seven additional Russian and Belarusian-speaking members of civil society and journalists living outside of Belarus and Russia who were targeted and/or infected with Pegasus spyware. Many of the targets publicly criticized the Russian government, including Russia’s invasion of Ukraine. These individuals, most of whom are currently living in exile, have faced intense threats from Russian and/or Belarusian state security services.
Threats at Home
Critics of the Russian and Belarusian governments typically face retaliation in the form of surveillance, detention, threats, violence, death, travel bans, financial surveillance, hacking, censorship, and political repression. After Russia’s 2022 invasion of Ukraine, the repression escalated, including the growing use of “Foreign Agent,” “Undesirable Organization,” “Fake News,” “Extremist,” and “Terrorist” designation laws that severely curtail the ability of designated media and civil society organizations to safely operate, communicate, collaborate, and fundraise. For transparency, we note that in March 2024 the Russian government designated the Munk School of Global Affairs & Public Policy at the University of Toronto (where The Citizen Lab is based) as an Undesirable Organization.
Threats in Exile
Recently, in light of growing repression, many individuals and groups that are perceived as enemies by the Russian and Belarusian governments have left to continue their work from abroad. Today, for example, many Russian and Belarusian independent media organizations operate from outside the country.
While geographic distance and borders provide a degree of protection from daily repression in Russia and Belarus, both regimes have a well-documented history of engaging in transnational repression against diaspora communities. This repression has included violent attacks, threats, suspected poisonings, and surveillance.
Organizing in exile may in fact increase certain digital risks, as groups are forced to rely almost exclusively on third-party platforms and tools to communicate and disseminate information, creating complex challenges for maintaining privacy and security. The shifting practices also introduce new opportunities for malicious actors to probe for and exploit vulnerabilities. There is already evidence of this kind of targeting. For example, Russian independent media organization Meduza reported an intense Distributed Denial of Service (DDoS) attack against their website during Russia’s 2024 presidential elections.
Pegasus Confirmations
We conclude with high confidence that the following individuals were targeted and/or infected with Pegasus spyware. We are publishing their names with their consent. More details about these individuals are available in Access Now’s report.
| Name | Description | Forensic Confirmation |
|---|---|---|
| Evgeny Erlikh | Israeli-Russian journalist, author and producer with Radio Free Europe / Radio Liberty’s (RFE/RL) Russian-Language network. Based in Riga, Latvia | Targeted and infected |
| Evgeny Pavlov | Latvian journalist, formerly freelancing for RFE/RL, previously with Novaya Gazeta Baltija. Based in Riga, Latvia | Targeted |
| Maria Epifanova | Russian journalist, general director of Novaya Gazeta Europe, director of Novaya Gazeta Baltija. Based in Riga, Latvia | Targeted and infected |
| Natallia Radzina | Belarusian journalist, editor in chief of Belarusian media website Charter97.org, recipient of CPJ’s International Press Freedom Award. Based in Warsaw, Poland | Targeted and infected |
| Andrei Sannikov | Belarusian opposition politician and activist. Sannikov ran for president in 2010, receiving the second-highest vote count after incumbent Alexander Lukashenko. Arrested after the election by the Belarusian KGB and held as a prisoner of conscience. Authorities also threatened to seize his 3-year-old son. Based in Warsaw, Poland | Targeted and infected |
| Anonymous 1 | Russian independent media journalist. Based in Vilnius, Lithuania | Targeted |
| Anonymous 2 | Belarusian civil society member. Based in Vilnius, Lithuania | Targeted and infected |
Individuals who were targeted with Pegasus (concluded with high confidence).
Note that a confirmation of targeting does not exclude the possibility of an infection, it simply indicates that no forensic traces associated with a successful infection were present at the time of analysis.
Patterns Linking the Pegasus Targeting
Five targeted devices recorded Apple IDs used by Pegasus operators in their hacking attempts. We believe that each Apple ID is only used by a single Pegasus operator, though a single Pegasus operator’s infrastructure might use multiple Apple IDs. In a pattern first spotted by the team at Access Now, Apple IDs used by operators in these cases overlap (Figure 1). The targeting timeframe, victim profiles, and overlap of operator Apple IDs suggest (but do not prove) the possibility that a single actor is responsible for these five attacks.
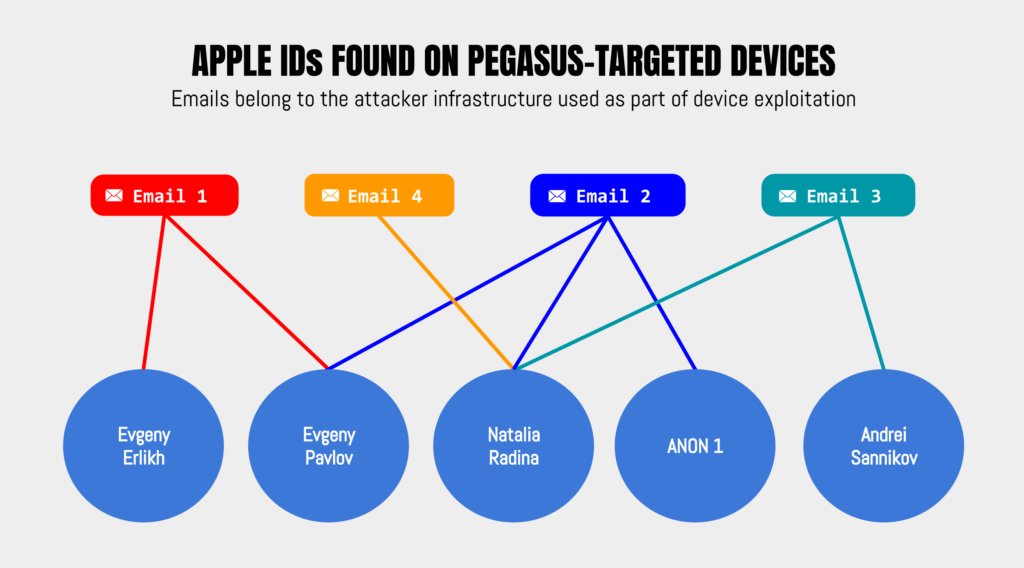
The Citizen Lab is not attributing these Pegasus spyware attacks to specific operators at this time. We note that Access Now’s report includes additional discussion of the possible Pegasus operators involved in these attacks.
Concerns Around This Pattern of Targeting
There are now eight documented cases of Pegasus mercenary spyware attacks against Russian and Belarusian-speaking opposition voices and independent media who live in exile or in the diaspora. The targets are already under intense threat from Russia and/or Belarus. Many have experienced other forms of surveillance and transnational repression. Several of the targets are renowned, respected members of independent media and opposition groups, raising an obvious concern regarding the legality, necessity, and proportionality of the pattern of hacking described in this report under international human rights law.
As the targeting is happening in Europe, where these individuals have sought safety, it raises important questions regarding whether host states are meeting their obligations under international human rights law to prevent and respond to these human rights violations, and more generally, to address, and not compound, the practice of digital transnational repression.
Suspect You May Be Targeted?
If you believe because of who you are or what you do that you may be targeted with mercenary spyware like Pegasus, you should take action and seek expert support.
If you are a member of civil society, such as a journalist, activist, dissident, or human rights defender, you can contact the Access Now Digital Security Helpline for expert advice and support.
Additionally, we encourage you to quickly harden your Apple devices by enabling Lockdown Mode. This mode helps protect you from advanced threats, and many users report to us that it is relatively easy to use. At the time of writing, The Citizen Lab has not discovered any cases where we believe spyware such as Pegasus has successfully infected a device while Lockdown Mode was enabled.
Android user?
Unfortunately, there is no feature similar to Lockdown Mode available on Android devices, so we recommend that you seek expert advice on whether resources, such as more security-focused operating systems, may be available for your specific device.
Whatever your preferred device(s), protecting yourself against sophisticated and unsophisticated attacks alike is a process, and we strongly encourage you to speak with someone that can help you tailor the steps you take to the threats you face.
Have You Received an Apple Threat Notification?
If you have received an Apple notification, we encourage you to consult this FAQ developed by Access Now and immediately seek expert support. We suggest that you wait to take drastic action until you have spoken with an expert. Actions such as factory resetting may or may not fully address your security concern, but they will almost certainly hinder any attempt by a trusted expert to help you figure out what may have happened.
Acknowledgements
We thank and acknowledge the Pegasus targets that graciously consented to share materials with us for analysis, discuss their cases, and to come forward. Without their participation, this investigation would have been impossible.
Special thanks to Nikolai Kvantiliani, and to the entire team at Access Now for their collaboration and assistance in this investigation.
Special thanks to Adam Senft and Alyson Bruce for editorial assistance and Mari Zhou for graphical assistance.
Special thanks to GreyEnabler and TNG.
