What does this research contribute to what we already know about WeChat?
WeChat is an app with many features. Previously, we studied the privacy issues surrounding its Mini Programs, as well as its surveillance and censorship of text and image messages. In this research, we focus on WeChat’s network encryption protocol and its security.
When information security researchers like us analyze the security of apps, one typeof analysis we perform is network traffic analysis, wherein we analyze what is sent by apps and how. This analysis can inform us about what data the app collects and with whom the data is shared.
Performing such an analysis on WeChat was initially not straightforward. Most apps today use industry standard Transport Layer Security (TLS) to encrypt the content of their network traffic, which normally protects eavesdroppers from reading the underlying data. When researchers wish to analyze their own traffic that their own apps are sending there already exist common tools to decrypt such content. However, such tools were inapplicable to WeChat because it uses a proprietary network encryption protocol different from TLS, called “MMTLS”. Prior to this research, little was known about MMTLS and there were no pre-existing tools to inspect content encrypted with MMTLS.
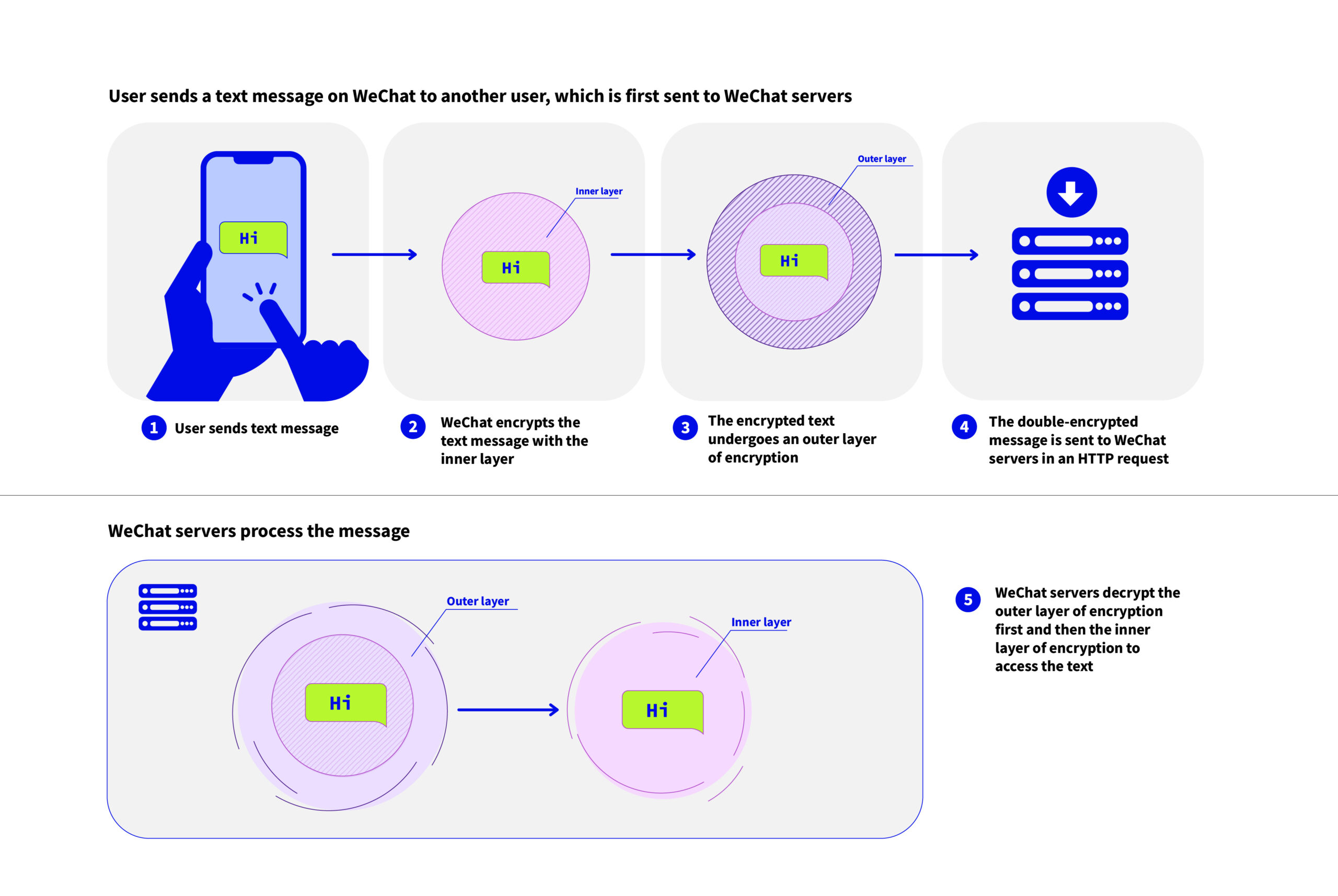
We reverse engineered the inner workings of WeChat’s network encryption and found minor issues with its security. We found that what we previously referred to as MMTLS was only the outer layer of encryption used by WeChat. Within MMTLS, we found a second layer of encryption that works entirely separately from MMTLS, called “Business-layer Encryption”. The two encryption systems are “wrapped” around each other like a Russian doll, i.e., the plaintext content would first be encrypted with the Business-layer Encryption, and the resulting Business-layer ciphertext would be used as input to MMTLS encryption, producing MMTLS ciphertext that would eventually be sent over the network.
We found several issues with the Business-layer Encryption, the most serious being a metadata leak, which leaves the user account ID and some other information unencrypted at this layer. We briefly studied an older WeChat version and found that it only contained the Business-layer Encryption. These findings suggest that Business-layer Encryption is older than MMTLS and that MMTLS was likely designed to remedy the shortcomings of Business-layer Encryption. Since MMTLS Encryption wraps around Business-layer Encryption, attempts to exploit the weaknesses of Business-layer Encryption would typically have to first defeat the protection provided by the MMTLS layer.
So far, we have not found serious security issues with MMTLS. Therefore, despite vulnerabilities in the Business Layer of encryption, these issues could not be utilized by an attacker, and does not affect the overall security of the app’s network encryption.
Is my communication on WeChat safe?
Everyone identifies with different threat models and thus have different definitions of “safe.” If you are concerned about the contents of your communication with another WeChat user being visible to a network eavesdropper, our research has shown that, despite having weaker protection against network eavesdropping compared to industry standard encryption protocols, WeChat’s encryption protocol is not vulnerable to any attack techniques known today.
WeChat uses a custom encryption protocol instead of the industry standard Transport Layer Security (TLS). Using a custom design for encryption is generally not recommended by information security experts, because a well-tested encryption protocol usually takes a multi-year joint effort by many researchers. It is unlikely that a single company is able to invest the same level of effort. We have also found minor issues in WeChat’s encryption protocol, while these same issues are not present in TLS.
In conclusion, despite that we did not find any significant weaknesses in WeChat’s encryption protocol, we still did find minor issues with it. These issues do not compromise the confidentiality of user communications. However, the same issues are not present within industry-standard TLS.
Can the Chinese government read my WeChat text messages?
On a regulatory level, because Tencent’s headquarter is located in China, it must comply with local law and respond to the Chinese government’s user data requests.
On a technical level, WeChat’s encryption protocol protects the communication between user devices and WeChat’s servers. It is not an end-to-end encryption system, which would encrypt data sent between two user devices. WeChat’s servers can and do decrypt and read each transmitted message. In the past, we found that WeChat uses a keyword-based detection system to censor private messages to and from Chinese users. The app also uses files sent by non-Chinese users to train their database of censored files for Chinese users.
What kind of user data does WeChat collect?
Please refer to our previous report which answers this question.
I have a phone with sensitive data. If I install WeChat, would it be able to steal that data?
Modern phone operating systems (OS) typically restrict apps from accessing sensitive user data (such as contacts and photos) and system resources (such as a geo-location service), as well as data stored in other apps (such as chat history in a chat app). Therefore, it is technically difficult for apps to access sensitive data without the user granting them permission. However, malicious apps could exploit vulnerabilities in OS protections and circumvent these access restrictions. Malicious apps might also trick the user into granting permission to access data.
It is outside our research scope to test whether WeChat exhibits these malicious behaviors. During our research we have not observed the malicious behaviors mentioned above.
To protect yourself from this kind of attack, we suggest:
- Make sure your phone’s OS version is currently supported by the vendor
- Keep your phone’s OS up-to-date
- Install apps from official sources (built-in app stores) instead of unofficial ones
- Check the app’s reputation before installing
- For highly sensitive information, use a separate dedicated device to handle it
Can WeChat harm my phone security and privacy even after uninstallation?
As mentioned above, modern phone operating systems implement system protection to control apps’ access to sensitive data. It is technically difficult for apps to maintain implants on a system after the app’s uninstallation. However, some malicious apps might try to do so by exploiting system vulnerabilities.
It is outside our research scope to test whether WeChat exhibits these malicious behaviors. However, throughout our research, we have not observed such malicious behavior.
What if I have other questions?
Read our full report and check out the FAQ from our previous WeChat report analyzing the app’s privacy.