Publications
Appendices for the report “Keep Calm and (Don’t) Enable Macros”
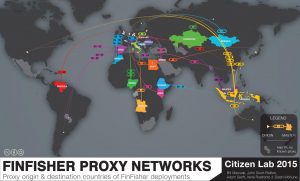
This post describes the results of Internet scanning we conducted to identify the users of FinFisher, a sophisticated and user-friendly spyware suite sold exclusively to governments.
This research note outlines what we know about the use of Hacking Team’s Remote Control System (RCS) by South Korea’s National Intelligence Service (NIS). The note synthesizes information found in publicly leaked materials, as well as our own research.
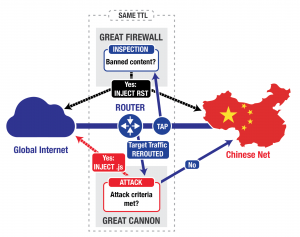
This post describes our analysis of China’s “Great Cannon,” our term for an attack tool that we identify as separate from, but co-located with, the Great Firewall of China. The first known usage of the Great Cannon is in the recent large-scale novel DDoS attack on both GitHub and servers used by GreatFire.org.
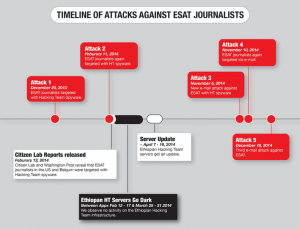
The research findings documented in this report suggest that Hacking Team may have continued to provide updated versions of its spyware to the same attacker who have targeted ESAT journalists based in the United States in 2014, despite reports of use of the spyware against journalists.