Publications
At USENIX Security 2014 Citizen Lab researchers presented two papers on targeted threats against civil society communities as part of a dedicated session on the topic entitled Tracking Targeted Attacks against Civilians and NGOs.
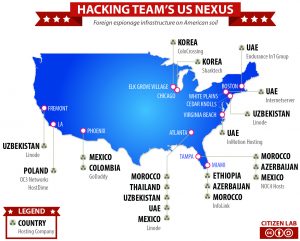
This report outlines an extensive US nexus for a network of servers forming part of the collection infrastructure of Hacking Team’s Remote Control System. The network, which includes data centers across the US, is used to obscure government clients of Hacking Team. It is used by at least 10 countries ranging from Azerbaijan and Uzbekistan to Korea, Poland and Ethiopia. In addition we highlight an intriguing US-only Hacking Team circuit.
In this report, we identified three instances where Ethiopian journalist group ESAT was targeted with spyware in the space of two hours by a single attacker. In each case the spyware appeared to be RCS (Remote Control System), programmed and sold exclusively to governments by Milan-based Hacking Team.
Citizen Lab is pleased to announce the release of “For Their Eyes Only: The Commercialization of Digital Spying.” The report features new findings, as well as consolidating a year of our research on the commercial market for offensive computer network intrusion capabilities developed by Western companies.
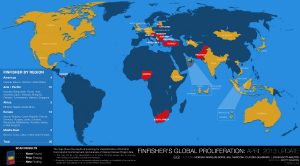
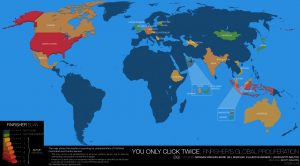
This post describes the results of a comprehensive global Internet scan for the command and control servers of FinFisher’s surveillance software. It also details the discovery of a campaign using FinFisher in Ethiopia that may have been used to target individuals linked to an opposition group. Additionally, it provides examination of a FinSpy Mobile sample found in the wild, which appears to have been used in Vietnam.