Publications
This report describes an espionage operation using government-exclusive spyware to target Mexican government food scientists and two public health advocates.
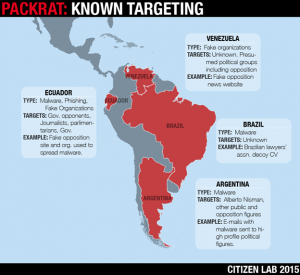
This report describes an extensive malware, phishing, and disinformation campaign active in several Latin American countries, including Ecuador, Argentina, Venezuela, and Brazil. The nature and geographic spread of the targets seems to point to a sponsor, or sponsors, with regional, political interests. The attackers, whom we have named Packrat, have shown a keen and systematic interest in the political opposition and the independent press in so-called ALBA countries (Bolivarian Alternative for the Americas), and their recently allied regimes.
We analyze a newly discovered Android implant that we attribute to Hacking Team and highlight the political subtext of the bait content and attack context. In addition, we expose the functionality and architecture of Hacking Team’s Remote Control system and operator tradecraft in never-before published detail.
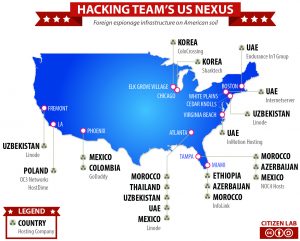
This report outlines an extensive US nexus for a network of servers forming part of the collection infrastructure of Hacking Team’s Remote Control System. The network, which includes data centers across the US, is used to obscure government clients of Hacking Team. It is used by at least 10 countries ranging from Azerbaijan and Uzbekistan to Korea, Poland and Ethiopia. In addition we highlight an intriguing US-only Hacking Team circuit.
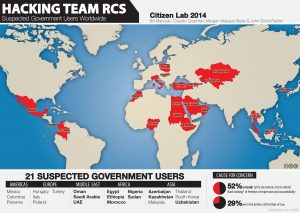
This post is the second in a series of posts that focus on the global proliferation and use of Hacking Team’s RCS spyware, which is sold exclusively to governments.