Publications
This campaign is the first documented case of one-click mobile exploits used to target Tibetan groups, and reflects an escalation in the sophistication of digital espionage threats targeting the community.
Endless Mayfly is an Iran-aligned network of inauthentic websites and online personas used to spread false and divisive information primarily targeting Saudi Arabia, the United States, and Israel. Using this network as an illustration, this report highlights the challenges of investigating and addressing disinformation from research and policy perspectives.
Investigation of a malware campaign targeting the Tibetan community and discussion of the challenges in analyzing closed espionage ecosystems.
This report describes an inexpensive and technically simple phishing operation. It shows that the continued low adoption rates for digital security features, such as two factor authentication, contribute to the low bar to entry for digital espionage.
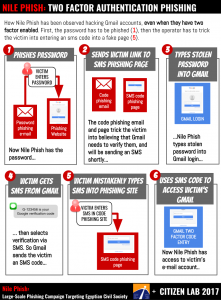
This report discusses the targeting of Egyptian NGOs by Nile Phish, a large-scale phishing campaign. Almost all of the targets we identified are also implicated in Case 173, a sprawling legal case brought by the Egyptian government against NGOs, which has been referred to as an “unprecedented crackdown” on Egypt’s civil society. Nile Phish operators demonstrate an intimate knowledge of Egyptian NGOs, and are able to roll out phishing attacks within hours of government actions, such as arrests.