Publications
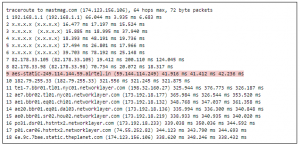
The Citizen Lab has analyzed recent targeted malware attacks against Tibetan organizations that share a common payload — LURK malware — and command-and-control server, as well as several other features.
OpenNet Initiative research has documented that web filtering applied by India-based ISPs is also filtering content for customers of an ISP in Oman. This “upstream filtering” is restricting access to news sites, political blogs and file sharing sites for customer’s of Omantel, who have limited opportunities for recourse. Combined with the significant filtering implemented by Omantel itself, this essentially puts users in Oman behind multiple layers of national-level filtering.
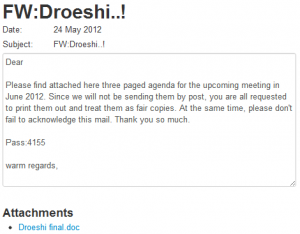
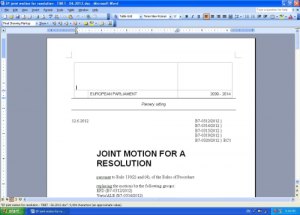
The Citizen Lab analyzes a recent targeted malware attack against the Tibetan community spoofing the June 14, 2012 resolution of the European Parliament (EP) on the human rights situation in Tibet. While such repurposing of authentic content for use as a malware delivery mechanism is not unusual, this incident raises serious questions surrounding the use of legitimate political resources for illegitimate ends.
This post is the first in a series of analyses that the Citizen Lab is preparing regarding the urgent and ongoing threat presented by information operations deployed against Tibetans and others who advocate for Tibetan rights and freedoms, including in Tibetan areas of China.
Additional evidence gathered by the Citizen Lab from Burma since the publication of Behind Blue Coat has provided further confirmation that Blue Coat’s devices are presently in use in the country.