Publications
We redact the last octet of the 186 IP addresses below that matched any of our fingerprints since 1 February 2014. IP Country Owner 101.99.83.12 MY PIRADIUS NET 103.1.185.xxx AU MAMMOTH MEDIA PTY LTD 106.186.118.191 JP LINODE LLC 106.186.16.48 JP LINODE LLC 106.186.17.xxx JP LINODE LLC 106.186.20.84 JP LINODE LLC 106.186.21.100 JP LINODE LLC 106.186.22.xxx […]
This report, Islands of Control, Islands of Resistance: Monitoring the 2013 Indonesian IGF, is the first in a series of Citizen Lab reports that apply a mixture of methods, from technical interrogation to field research and social and legal analyses, to study information controls in and around particular events. This report focuses on information controls in and around Indonesia’s hosting of the United Nations Internet Governance Forum (IGF).
Governments’ use of biometric systems have raised privacy concerns and the need for greater transparency and accountability. This is because these systems collect and store individuals’ physical traits such as fingerprints, facial recognition, iris scans, and other personal characteristics. Biometric identification has been criticized as being error-prone and unreliable, as well as being fundamentally detrimental to privacy, free expression, and the right to anonymity, especially with regards to vulnerable individuals such as dissidents, whistleblowers, and journalists. Members of the Cyber Stewards Network are active in efforts to raise awareness on the use of biometric systems and surveillance technologies.
Cyber Steward Network partner Walid Al-Saqaf writes about the recent launch of Yemen’s chapter of the Internet Society for Global Voices Advocacy.
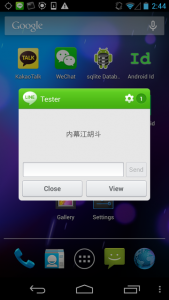
This post is an introduction to Asia Chats, a research project analyzing information controls and privacy in mobile messaging applications used in Asia. The project will produce a series of reports that will begin with a focus on WeChat, LINE, and KakaoTalk. Reports will include analysis based on our technical investigation of censorship or surveillance functionality, assessment of privacy issues surrounding these applications’ use and storage of user data, and comparison of the terms of service and privacy policies of the applications.