Publications
This report describes a campaign of targeted spyware attacks carried out by a sophisticated operator, which we call Stealth Falcon. The attacks have been conducted from 2012 until the present, against Emirati journalists, activists, and dissidents.
This report describes the latest iteration in a long-running espionage campaign against the Tibetan community. We describe how the attackers continuously adapt their campaigns to their targets, shifting tactics from document-based malware to conventional phishing
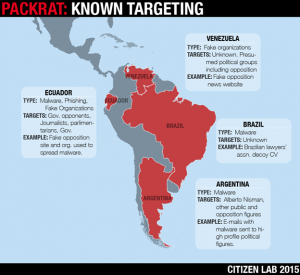
This report describes an extensive malware, phishing, and disinformation campaign active in several Latin American countries, including Ecuador, Argentina, Venezuela, and Brazil. The nature and geographic spread of the targets seems to point to a sponsor, or sponsors, with regional, political interests. The attackers, whom we have named Packrat, have shown a keen and systematic interest in the political opposition and the independent press in so-called ALBA countries (Bolivarian Alternative for the Americas), and their recently allied regimes.
A second audit of South Korea’s Smart Sheriff application reveals that there are numerous unresolved vulnerabilities that put minor children and parental users of the application at serious risk.
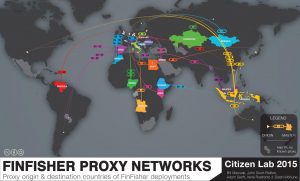
This post describes the results of Internet scanning we conducted to identify the users of FinFisher, a sophisticated and user-friendly spyware suite sold exclusively to governments.