Publications
In the past 24 hours The Citizen Lab has identified a maliciously repackaged copy of the popular circumvention software Psiphon 3. This post describes the malware and outlines steps to be taken.
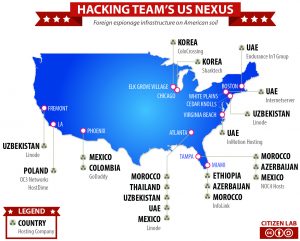
This report outlines an extensive US nexus for a network of servers forming part of the collection infrastructure of Hacking Team’s Remote Control System. The network, which includes data centers across the US, is used to obscure government clients of Hacking Team. It is used by at least 10 countries ranging from Azerbaijan and Uzbekistan to Korea, Poland and Ethiopia. In addition we highlight an intriguing US-only Hacking Team circuit.
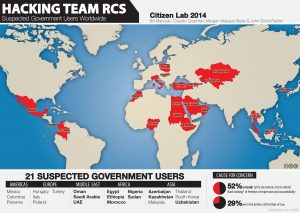
This post is the second in a series of posts that focus on the global proliferation and use of Hacking Team’s RCS spyware, which is sold exclusively to governments.
In this report, we identified three instances where Ethiopian journalist group ESAT was targeted with spyware in the space of two hours by a single attacker. In each case the spyware appeared to be RCS (Remote Control System), programmed and sold exclusively to governments by Milan-based Hacking Team.
In this report, Citizen Lab researchers Morgan Marquis-Boire and John Scott-Railton and EFF Global Policy Analyst Eva Galperin outline how pro-government attackers have targeted the Syrian opposition, as well as NGO workers and journalists, with social engineering and “Remote Access Tools” (RAT)