Publications
This report describes a malware operation against the Syrian Opposition. We name the operator Group5, and suspect they have not been previously-reported. Group5 used “just enough” technical sophistication, combined with social engineering, to target computers and mobile phones with malware.
This report analyzes a campaign of targeted attacks against an NGO working on environmental issues in Southeast Asia. Our analysis reveals connections between these attacks, recent strategic web compromises against Burmese government websites, and previous campaigns targeting groups in the Tibetan community.
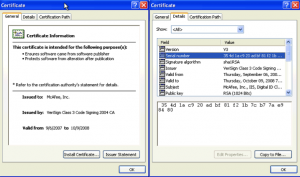
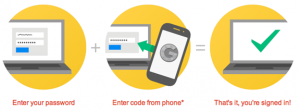
This report describes an elaborate phishing campaign using two-factor authentication against targets in Iran’s diaspora, and at least one Western activist.
This post analyzes targeted malware attacks against groups in the Tibetan diaspora and Hong Kong that leverage the CVE-2014-4114 vulnerability
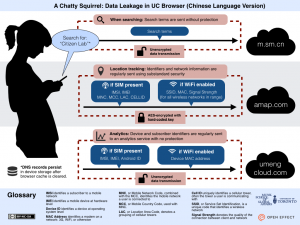
UC Browser is the most popular mobile web browser in China and India, boasting over 500 million users. This report provides a detailed analysis of how UC Browser manages and transmits user data, particularly private data, during its operation. Our research was prompted by revelations in a document leaked by Edward Snowden on which the Canadian Broadcasting Corporation (CBC) was preparing a story.