Publications
Hundreds of members of the Tibetan community are being targeted by email-based malware attacks that leverage the March 10 Tibetan Uprising anniversary as a theme. This report analyzes two March 10 related attacks. One using a new malware family we call MsAttacker , and another using the ShadowNet malware family and command and control infrastructure related to previous campaigns that targeted the Tibetan community.
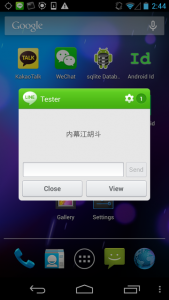
We analyze a newly discovered Android implant that we attribute to Hacking Team and highlight the political subtext of the bait content and attack context. In addition, we expose the functionality and architecture of Hacking Team’s Remote Control system and operator tradecraft in never-before published detail.
This post is an introduction to Asia Chats, a research project analyzing information controls and privacy in mobile messaging applications used in Asia. The project will produce a series of reports that will begin with a focus on WeChat, LINE, and KakaoTalk. Reports will include analysis based on our technical investigation of censorship or surveillance functionality, assessment of privacy issues surrounding these applications’ use and storage of user data, and comparison of the terms of service and privacy policies of the applications.
In this post, we report on “Surtr”, a malware family that has been used in targeted malware campaigns against the Tibetan community since November 2012