Publications
Two Egyptians—exiled politician Ayman Nour and the host of a popular news program (who wishes to remain anonymous)—were hacked with Predator spyware, built and sold by the previously little-known mercenary spyware developer Cytrox. The phone of Ayman Nour was simultaneously infected with both Cytrox’s Predator and NSO Group’s Pegasus spyware, operated by two different government clients.
While analyzing the phone of a Saudi activist infected with NSO Group’s Pegasus spyware, we discovered a zero-day zero-click exploit against iMessage. The exploit, which we call FORCEDENTRY, targets Apple’s image rendering library, and was effective against Apple iOS, MacOS and WatchOS devices.
We identified nine Bahraini activists whose iPhones were successfully hacked with NSO Group’s Pegasus spyware between June 2020 and February 2021. The hacked activists included three members of Waad (a secular Bahraini political society), three members of the Bahrain Center for Human Rights, two exiled Bahraini dissidents, and one member of Al Wefaq (a Shiite Bahraini political society).
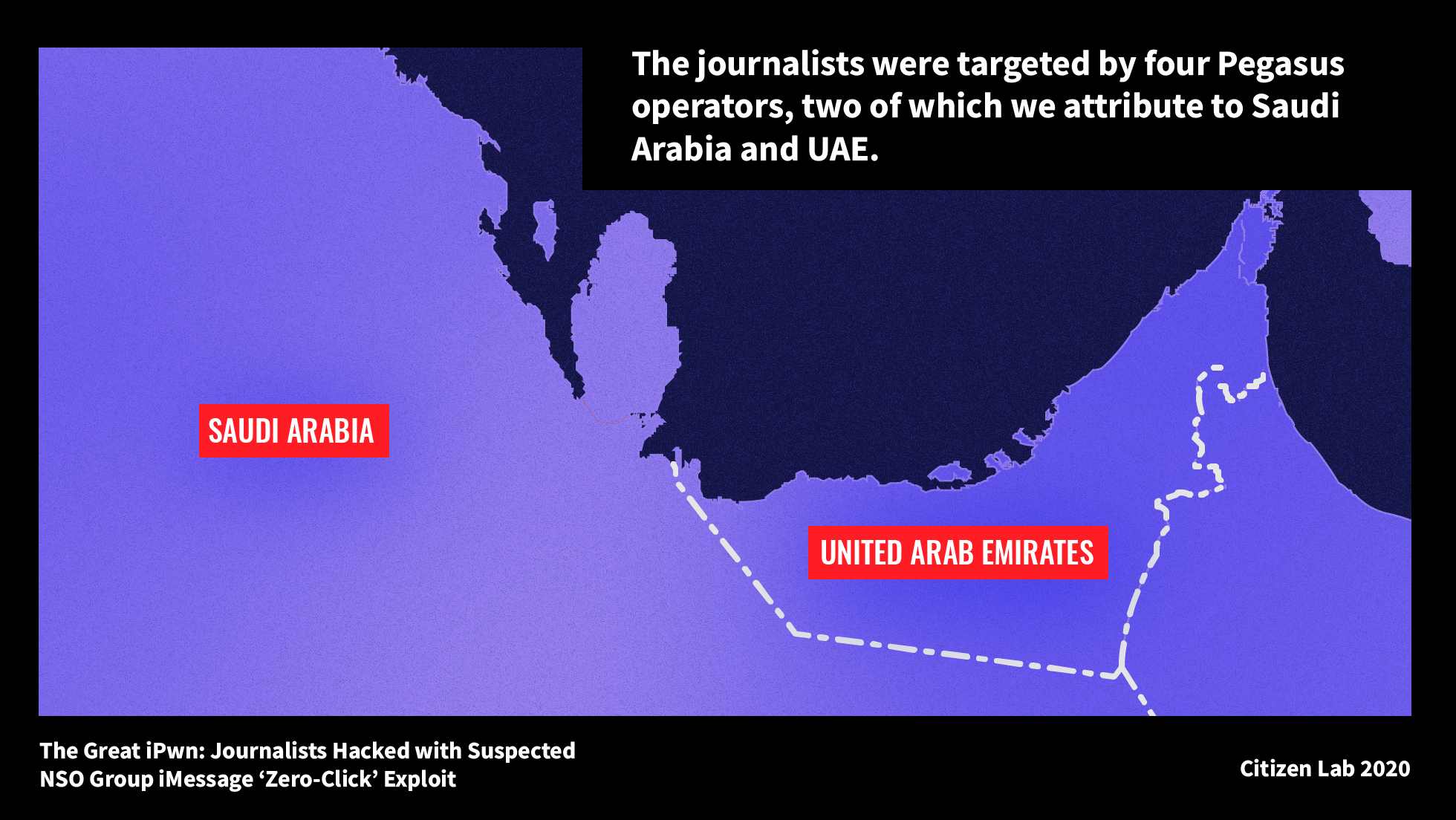
Government operatives used NSO Group’s Pegasus spyware to hack 36 personal phones belonging to journalists, producers, anchors, and executives at Al Jazeera. The journalists were hacked by four Pegasus operators, including one operator MONARCHY that we attribute to Saudi Arabia, and one operator SNEAKY KESTREL that we attribute to the United Arab Emirates.
This annotated bibliography compiles and summarizes relevant literature on “digital transnational repression” (i.e., where states seek to exert pressure—using digital tools—on citizens living abroad in order to constrain, limit, or eliminate political or social action that threatens regime stability or social and cultural norms within the country). While transnational repression itself is not a new phenomenon, there has been limited research on how such repression is enabled and expanded by digital tools.