FinFisher
A public interest litigation case launched by CSN Partner Bytes For All (B4A) at the Lahore High Court has been met with obstacles during court proceedings. Despite a court order to look into the matter and produce a report in one month, the Pakistan Telecommunications Authority (PTA) has failed to do so.
An article on commercial spyware in Voice of America cited Citizen Lab research into ‘lawful intercept’ spyware such as FinSpy.
Citizen Lab research into FinSpy, a suite of surveillance software marketed exclusively to governments by the Gamma Group of Companies, has helped in the recent lawsuit put forth by an American citizen living in Maryland.
Citizen Lab’s Bill Marczak helped Privacy International scan Ethiopian refugee Tadesse Biru Kersmo’s computer, and they found traces that showed FinSpy had been operating in June 2012 over two days while he was in the UK.
An article in the Washington Post, titled “Research shows how MacBook Webcams can spy on their users without warning,” discussed two of the Citizen Lab’s research outputs.
On May 13, 2013, Bytes for All (B4A), a Pakistani civil society group and partner in the Cyber Stewards Network, filed a petition with the Lahore High Court on the possible use of the FinFisher product suite in Pakistan. B4A has advocated for the rights of Pakistani netizens to browse the Internet free of censorship and surveillance through numerous court and government actions, including a recent petition submitted in January 2013 in protest of the ongoing censorship of YouTube.
Citizen Lab Director Ron Deibert spoke about how repressive governments around the world have been getting assistance from Western technology companies.
Privacy International have filed an application for judicial review of HM Revenue & Customs (HMRC) refusal to release information about the potentially unlawful export of Gamma International’s FinFisher surveillance technology.
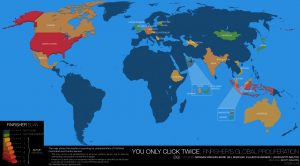
This post describes the results of a comprehensive global Internet scan for the command and control servers of FinFisher’s surveillance software. It also details the discovery of a campaign using FinFisher in Ethiopia that may have been used to target individuals linked to an opposition group. Additionally, it provides examination of a FinSpy Mobile sample found in the wild, which appears to have been used in Vietnam.
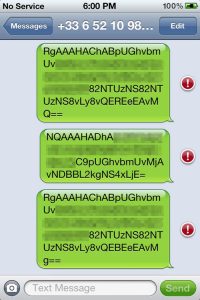
This report, written and coordinated by Citizen Lab Technical Advisor Morgan Marquis-Boire, analyzes several samples we believe to be mobile variants of the FinFisher Spy Kit targeting iPhone, Android, Blackberry, Windows Mobile and Symbian platforms. It is a follow-on to a previous research brief, From Bahrain with Love: FinFisher's Spy Kit Exposed?, that analyzed several pieces of malware targeting Bahraini dissidents.