malware
Our investigation of a spearphishing campaign that targeted senior members of the World Uyghur Congress in March 2025 reveals a highly-customized attack delivery method. The ruse used by attackers replicates a pattern in which threat actors weaponize software and websites aimed at preserving and supporting marginalized and repressed cultures to target those same communities.
This report reveals a campaign of reconnaissance, phishing, and malware operations that use content and domains made to mimic Chinese language news websites.
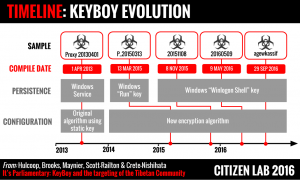
In this report we track a malware operation targeting members of the Tibetan Parliament that used known and patched exploits to deliver a custom backdoor known as KeyBoy. We analyze multiple versions of KeyBoy revealing a development cycle focused on avoiding basic antivirus detection.
This report describes a malware operation against the Syrian Opposition. We name the operator Group5, and suspect they have not been previously-reported. Group5 used “just enough” technical sophistication, combined with social engineering, to target computers and mobile phones with malware.
In this research note, we analyze a malware campaign targeting Hong Kong democracy activists. Two new malware families are used in the campaign that we name UP007 and SLServer. Previous reports have shown overlap in the tactics, tools, and procedures used in this campaign in other operations targeting groups in Burma, Hong Kong, and the Tibetan community.
This post analyzes targeted malware attacks against groups in the Tibetan diaspora and Hong Kong that leverage the CVE-2014-4114 vulnerability
Hundreds of members of the Tibetan community are being targeted by email-based malware attacks that leverage the March 10 Tibetan Uprising anniversary as a theme. This report analyzes two March 10 related attacks. One using a new malware family we call MsAttacker , and another using the ShadowNet malware family and command and control infrastructure related to previous campaigns that targeted the Tibetan community.
This report describes a malware attack on a Syrian citizen media group critical of Islamic State of Iraq and Syria (ISIS). Though we are unable to conclusively attribute the attack to ISIS or its supporters, a link to ISIS is plausible. The malware used in the attack differs substantially from campaigns linked to the Syrian regime, and the attack is against a group that is an active target of ISIS forces. In the interest of highlighting a developing threat, this post analyzes the attack and provides a list of Indicators of Compromise.
We analyze a newly discovered Android implant that we attribute to Hacking Team and highlight the political subtext of the bait content and attack context. In addition, we expose the functionality and architecture of Hacking Team’s Remote Control system and operator tradecraft in never-before published detail.
In the past 24 hours The Citizen Lab has identified a maliciously repackaged copy of the popular circumvention software Psiphon 3. This post describes the malware and outlines steps to be taken.