malware
In this report, Citizen Lab researchers Morgan Marquis-Boire and John Scott-Railton and EFF Global Policy Analyst Eva Galperin outline how pro-government attackers have targeted the Syrian opposition, as well as NGO workers and journalists, with social engineering and “Remote Access Tools” (RAT)
In this post, we report on “Surtr”, a malware family that has been used in targeted malware campaigns against the Tibetan community since November 2012
The Citizen Lab is pleased to announce the publication of A Call to Harm: New Malware Attacks Against the Syrian Opposition. This research report by Morgan Marquis-Boire and John Scott-Railton examines two recent cyber attacks targeting the Syrian opposition: malware masquerading as the circumvention tool Freegate and a campaign masquerading as a call to arms by a pro-opposition cleric.
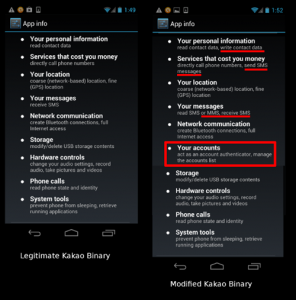
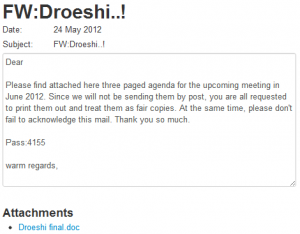
This blog post reports on a malware attack in which a compromised version of Kakao Talk, an Android-based mobile messaging client, was sent in a highly-targeted email to a prominent individual in the Tibetan community. The malware is designed to send a user’s contacts, SMS message history, and cellular network location to attackers. This post was updated on 18 April 2013.
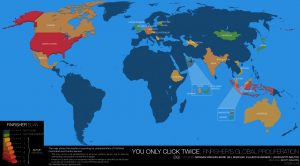
This post describes the results of a comprehensive global Internet scan for the command and control servers of FinFisher’s surveillance software. It also details the discovery of a campaign using FinFisher in Ethiopia that may have been used to target individuals linked to an opposition group. Additionally, it provides examination of a FinSpy Mobile sample found in the wild, which appears to have been used in Vietnam.
In this research brief, Seth Hardy describes malware (“GLASSES”) sent in 2010 that is a simple downloader closely related to malware described by Mandiant in their APT1 report. GLASSES appears to be a previous version of malware called GOGGLES by Mandiant, and was sent in a highly targeted email to a Tibetan human rights organization, demonstrating that APT1 is involved in more than just industrial and corporate espionage.
The Citizen Lab has analyzed recent targeted malware attacks against Tibetan organizations that share a common payload — LURK malware — and command-and-control server, as well as several other features.
Security Researcher and Citizen Lab Technical Advisor Morgan Marquis-Boire warns that this Trojan has been specifically crafted to target people attempting to evade government censorship. Last updated: May 30.