Pegasus
This report details how colleagues of a slain Mexican journalist investigating cartels were targeted with NSO Group’s Pegasus spyware in the days after his killing.
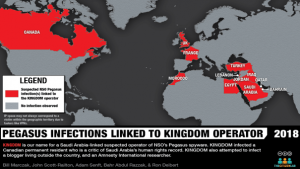
In this report, we describe how Canadian permanent resident and Saudi dissident Omar Abdulaziz was targeted with a fake package delivery notification. We assess with high confidence that Abdulaziz’s phone was infected with NSO’s Pegasus spyware. We attribute this infection to a Pegasus operator linked to Saudi Arabia.
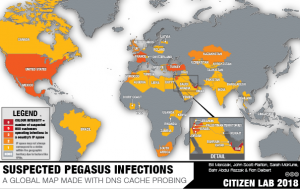
In this post, we develop new Internet scanning techniques to identify 45 countries in which operators of NSO Group’s Pegasus spyware may be conducting operations.
Citizen Lab validates Amnesty International investigation showing targeting of staff member and Saudi activist with NSO Group’s technology.
On August 30, 2017 Citizen Lab’s Reckless V report received front page coverage on the New York Times. This report revealed that Claudio X. González, Director of a prominent anti-corruption organization, was targeted with government-exclusive spyware produced by the NSO Group. This is the latest in a growing case that reveals lawyers, journalists, human rights advocates, international […]
Claudio X. González, the director of Mexicanos Contra la Corrupción y la Impunidad (MCCI: Mexicans Against Impunity and Corruption), becomes the 22nd known individual abusively targeted with NSO’s spyware technology in Mexico.
Lawyers representing the families of three slain Mexican women were sent infection attempts with NSO Group’s Pegasus spyware after questioning official accounts of the killings.
The international investigation into the 2014 Iguala Mass Disappearance was targeted with infection attempts using spyware developed by the NSO group.
NSO Group’s Pegasus spyware and exploit framework were used in infection attempts against Mexican senators and senior politicians in June and July 2016.
Uncovering an operation using NSO Group’s Pegasus spyware and Trident exploit framework to target Mexican journalists, lawyers, and even a minor child.