phishing
In May 2025, Keir Giles, a well-known expert on Russian military operations, was targeted with a highly sophisticated and personalized phishing attack. Using a method not previously observed by the Citizen Lab, the attacker posed as a U.S. State Department employee to convince Mr. Giles to create and send app-specific passwords for his email accounts, bypassing multi-factor authentication. Google spotted and blocked the attack, attributing it to a Russian state-backed operator.
Our investigation of a spearphishing campaign that targeted senior members of the World Uyghur Congress in March 2025 reveals a highly-customized attack delivery method. The ruse used by attackers replicates a pattern in which threat actors weaponize software and websites aimed at preserving and supporting marginalized and repressed cultures to target those same communities.
A sophisticated spear phishing campaign has been targeting Western and Russian civil society. In collaboration with Access Now, and with the participation of numerous civil society organizations, we uncover this operation and link it to COLDRIVER, a group attributed by multiple governments to the Russian Federal Security Service (FSB).
This campaign is the first documented case of one-click mobile exploits used to target Tibetan groups, and reflects an escalation in the sophistication of digital espionage threats targeting the community.
Investigation of a malware campaign targeting the Tibetan community and discussion of the challenges in analyzing closed espionage ecosystems.
This report describes an inexpensive and technically simple phishing operation. It shows that the continued low adoption rates for digital security features, such as two factor authentication, contribute to the low bar to entry for digital espionage.
This report reveals a campaign of reconnaissance, phishing, and malware operations that use content and domains made to mimic Chinese language news websites.
Documents stolen from a prominent journalist and critic of the Russian government were manipulated and then released as a “leak” to discredit domestic and foreign critics of the government. We call this technique “tainted leaks.”
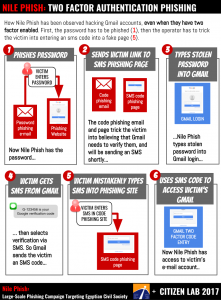
This report discusses the targeting of Egyptian NGOs by Nile Phish, a large-scale phishing campaign. Almost all of the targets we identified are also implicated in Case 173, a sprawling legal case brought by the Egyptian government against NGOs, which has been referred to as an “unprecedented crackdown” on Egypt’s civil society. Nile Phish operators demonstrate an intimate knowledge of Egyptian NGOs, and are able to roll out phishing attacks within hours of government actions, such as arrests.
This report describes the latest iteration in a long-running espionage campaign against the Tibetan community. We describe how the attackers continuously adapt their campaigns to their targets, shifting tactics from document-based malware to conventional phishing