Report
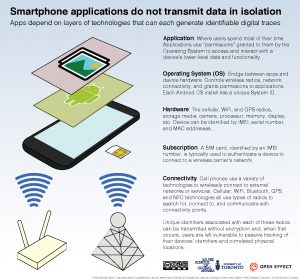
This document describes key identifiers used by mobile devices, highlights some identifiers that are accessible, and often collected, by various parties and the risks associated with the widespread transmission and use of these identifiers.
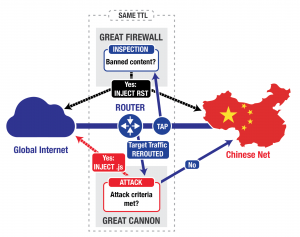
This post describes our analysis of China’s “Great Cannon,” our term for an attack tool that we identify as separate from, but co-located with, the Great Firewall of China. The first known usage of the Great Cannon is in the recent large-scale novel DDoS attack on both GitHub and servers used by GreatFire.org.
Hundreds of members of the Tibetan community are being targeted by email-based malware attacks that leverage the March 10 Tibetan Uprising anniversary as a theme. This report analyzes two March 10 related attacks. One using a new malware family we call MsAttacker , and another using the ShadowNet malware family and command and control infrastructure related to previous campaigns that targeted the Tibetan community.
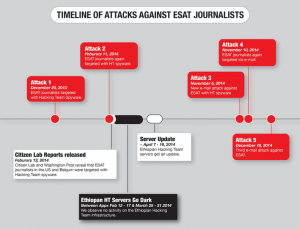
The research findings documented in this report suggest that Hacking Team may have continued to provide updated versions of its spyware to the same attacker who have targeted ESAT journalists based in the United States in 2014, despite reports of use of the spyware against journalists.
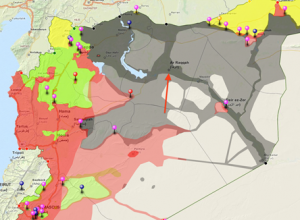
This report describes a malware attack on a Syrian citizen media group critical of Islamic State of Iraq and Syria (ISIS). Though we are unable to conclusively attribute the attack to ISIS or its supporters, a link to ISIS is plausible. The malware used in the attack differs substantially from campaigns linked to the Syrian regime, and the attack is against a group that is an active target of ISIS forces. In the interest of highlighting a developing threat, this post analyzes the attack and provides a list of Indicators of Compromise.
This report describes a malware attack on a Syrian citizen media group critical of Islamic State of Iraq and Syria (ISIS). Though we are unable to conclusively attribute the attack to ISIS or its supporters, a link to ISIS is plausible. The malware used in the attack differs substantially from campaigns linked to the Syrian regime, and the attack is against a group that is an active target of ISIS forces. In the interest of highlighting a developing threat, this post analyzes the attack and provides a list of Indicators of Compromise.
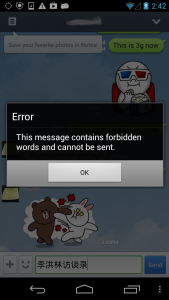
This report is part of a series which analyzes regionally-based keyword censorship in LINE, a mobile messaging application developed by LINE Corporation. The most recent update to the censorship keyword list include a number of new entries as well as the introduction of regular expressions for more advanced keyword matching.
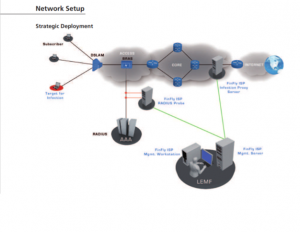
This report provides a detailed analysis of two products sold for facilitating targeted surveillance known as network injection appliances. These products allow for the easy deployment of targeted surveillance implants and are being sold by commercial vendors to countries around the world. Compromising a target becomes as simple as waiting for the user to view unencrypted content on the Internet.
In this report, we update the results of our June 2014 network measurement tests in Iraq in reaction to the ongoing insurgency in the country, and analyze two mobile applications, FireChat and Dawn of Glad Tidings.
In this post we report updates on how LINE, KakaoTalk, OneDrive and Flickr are being disrupted in China. We find that Flickr and OneDrive remain consistently blocked, but LINE and KakaoTalk show inconsistent fluctuation between accessibility and inaccessibility. We also analyze security and privacy of FireChat and test accessibility of the service in China.