Report
This post analyzes the multistakeholder participation in the 2013 IGF in Indonesia, which has been lauded as a model for how different stakeholder groups can operate at these events, and discusses developments in the country’s Internet governance agenda.
This blog post seeks to map out the infrastructure and governance of ICTs in the country, and explores the trends and challenges regarding the right to freedom of expression and access to information, that is grounded in the universal human rights framework.
An Indonesian translation of this post is available here.
Terjemahan dalam bahasa Indonesia dari halaman ini tersedia disini.
Building on past network measurements, legal, and policy analyses undertaken by the OpenNet Initiative, we set out to apply a mixed-methods approach to better understand the current situation in Indonesia. Our analysis is set in the context not only of the 2013 IGF, but amidst increasingly intense debates about free expression and access to information, and rapid technological change and development.
This post will summarize Citizen Lab’s prior research on surveillance in Indonesia, including documented evidence of FinFisher command and control servers and Blue Coat Systems devices on IPs owned by Indonesian ISPs. It will then identify recent trends in Indonesian surveillance practices, laws, and regulations that provide potential avenues for further research.
On October 22-25, 2013, Indonesia will host the eighth annual Internet Governance Forum (IGF), a multi-stakeholder dialogue on the issues and policies of Internet governance. The main theme of this year’s IGF is “Building Bridges: Enhancing Multi-stakeholder Cooperation for Growth and Sustainable Development.”
This post is the first in a series that will explore online freedom of expression and the state of information controls in Indonesia in the context of their role as host of the IGF.
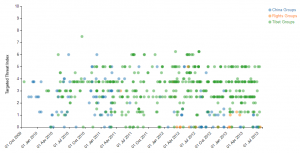
The Targeted Threat Index is a metric for assigning an overall threat ranking score to email messages that deliver malware to a victim’s computer. The TTI metric was first introduced at SecTor 2013 as part of the talk “RATastrophe: Monitoring a Malware Menagerie” by Katie Kleemola, Seth Hardy, and Greg Wiseman.
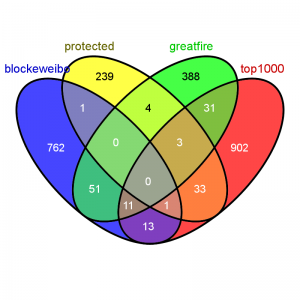
This project is a large-scale comparison of the three services, matching thousands of Chinese-language Wikipedia articles with their in-China counterparts, in order to identify the “content gaps” in the two baike. The difficulties of identifying traditional cases of information control in environments with distributed oversight like online enclopedias will be discussed. The research methodology and some of the initial results (including tables of possibly censored articles) will also be presented.
In this post, we report on “Surtr”, a malware family that has been used in targeted malware campaigns against the Tibetan community since November 2012
The Citizen Lab is pleased to announce the release of Some Devices Wander by Mistake: Planet Blue Coat Redux. In this report, we use a combination of network measurement and scanning methods and tools to identify instances of Blue Coat ProxySG and PacketShaper devices. This equipment can be used to secure and maintain networks, but can also be used to implement politically-motivated restrictions on access to information, and monitor and record private communications. We found Blue Coat devices on public networks of 83 countries. Included in these countries are regimes with questionable human rights records, and three countries that are subject to US sanctions: Iran, Syria, and Sudan.
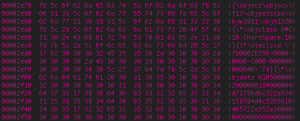
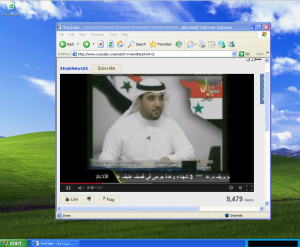
The Citizen Lab is pleased to announce the publication of A Call to Harm: New Malware Attacks Against the Syrian Opposition. This research report by Morgan Marquis-Boire and John Scott-Railton examines two recent cyber attacks targeting the Syrian opposition: malware masquerading as the circumvention tool Freegate and a campaign masquerading as a call to arms by a pro-opposition cleric.