Report
Our analysis of spyware covertly implanted on a phone returned to a Russian programmer after he was released from custody, finds that the spyware placed on his device allows the operator to track a target device’s location, record phone calls, keystrokes, and read messages from encrypted messaging apps, among other capabilities.
Drawing on the lived experiences of 85 women human rights defenders originating from 24 countries of origin and residing in 23 host countries, we examine how gender and sexuality play a central role in digital transnational repression.
We analyze the system Amazon deploys on the US “amazon.com” storefront to restrict shipments of certain products to specific regions. We found 17,050 products that Amazon restricted from being shipped to at least one world region. – While many of the shipping restrictions are related to regulations involving WiFi, car seats, and other heavily regulated product categories, the most common product category restricted by Amazon in our study was books.
This report performs the first public analysis of MMTLS, the main network protocol used by WeChat, an app with over one billion users. The report finds that MMTLS is a modified version of TLS, however some of the modifications have introduced cryptographic weaknesses.
A sophisticated spear phishing campaign has been targeting Western and Russian civil society. In collaboration with Access Now, and with the participation of numerous civil society organizations, we uncover this operation and link it to COLDRIVER, a group attributed by multiple governments to the Russian Federal Security Service (FSB).
In a joint investigation with Access Now, we found that seven Russian and Belarusian-speaking independent journalists and opposition activists based in Europe were targeted and/or infected with NSO Group’s Pegasus mercenary spyware.
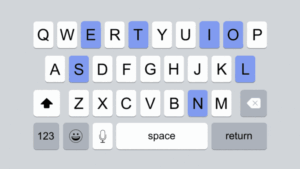
In this report, we examine cloud-based pinyin keyboard apps from nine vendors (Baidu, Honor, Huawei, iFlyTek, OPPO, Samsung, Tencent, Vivo, and Xiaomi) for vulnerabilities in how the apps transmit user keystrokes. Our analysis found that eight of the nine apps identified contained vulnerabilities that could be exploited to completely reveal the contents of users’ keystrokes in transit. We estimate that up to one billion users could be vulnerable to having all of their keystrokes intercepted, constituting a tremendous risk to user security.
A network of at least 123 websites operated from within the People’s Republic of China while posing as local news outlets in 30 countries across Europe, Asia, and Latin America, disseminates pro-Beijing disinformation and ad hominem attacks within much larger volumes of commercial press releases. We name this campaign PAPERWALL. We attribute the PAPERWALL campaign to Shenzhen Haimaiyunxiang Media Co., Ltd., aka Haimai, a PR firm in China based on digital infrastructure linkages between the firm’s official website and the network. These findings confirm the increasingly important role private firms play in the realm of digital influence operations and the propensity of the Chinese government to make use of them.
As part of our ongoing project monitoring changes to Chinese search censorship, we tracked changes to censorship following Li Keqiang’s death across seven Internet platforms: Baidu, Baidu Zhidao, Bilibili, Microsoft Bing, Jingdong, Sogou, and Weibo. We found that some keyword combinations in search queries triggers hard censorship whereas others trigger soft censorship. Our results demonstrate China’s ongoing efforts to push state-sanctioned narratives concerning politically sensitive topics, impacting the integrity of the online information environment.
This report provides a comprehensive guide to geolocation-related threats sourced from 3G, 4G, and 5G network operators. Case studies, references, examples, and evidence are provided to give a complete and contextual understanding of mobile network-based location tracking in order to formulate policies and actions that protect civil society from current and future geolocation surveillance.