Report
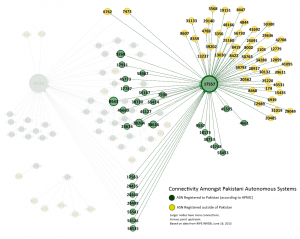
A new Citizen Lab report, entitled O Pakistan, We Stand on Guard for Thee: An Analysis of Canada-based Netsweeper’s Role in Pakistan’s Censorship Regime, has found that Canada-based Netsweeper filtering products have been installed in Pakistan, and are being used for filtering political and social web content.
As citizens in China commemorate the twenty-fourth anniversary of June 4th today, we identified 71 keywords that are currently blocked from searching on Sina Weibo.
Citizen Lab is pleased to announce the release of “For Their Eyes Only: The Commercialization of Digital Spying.” The report features new findings, as well as consolidating a year of our research on the commercial market for offensive computer network intrusion capabilities developed by Western companies.
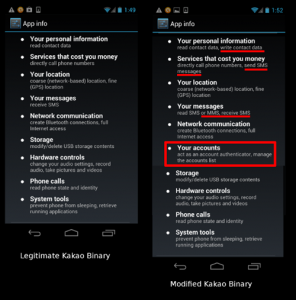
This blog post reports on a malware attack in which a compromised version of Kakao Talk, an Android-based mobile messaging client, was sent in a highly-targeted email to a prominent individual in the Tibetan community. The malware is designed to send a user’s contacts, SMS message history, and cellular network location to attackers. This post was updated on 18 April 2013.
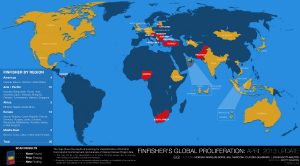
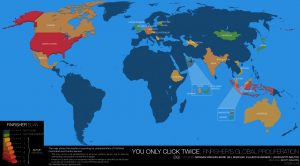
This post describes the results of a comprehensive global Internet scan for the command and control servers of FinFisher’s surveillance software. It also details the discovery of a campaign using FinFisher in Ethiopia that may have been used to target individuals linked to an opposition group. Additionally, it provides examination of a FinSpy Mobile sample found in the wild, which appears to have been used in Vietnam.
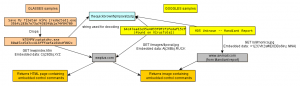
In this research brief, Seth Hardy describes malware (“GLASSES”) sent in 2010 that is a simple downloader closely related to malware described by Mandiant in their APT1 report. GLASSES appears to be a previous version of malware called GOGGLES by Mandiant, and was sent in a highly targeted email to a Tibetan human rights organization, demonstrating that APT1 is involved in more than just industrial and corporate espionage.
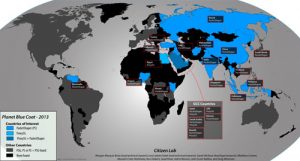
Blue Coat Devices capable of filtering, censorship, and surveillance are being used around the world. 61 of these Blue Coat appliances are on public or government networks in countries with a history of concerns over human rights, surveillance, and censorship. Our findings support the need for national and international scrutiny of Blue Coat implementations in the countries we have identified, and a closer look at the global proliferation of “dual-use” information and communication technologies.
In this report, Citizen Lab Security Researcher Morgan Marquis-Boire describes analysis performed on malicious software used to compromise a high profile dissident residing in the United Arab Emirates. The findings indicate that the software is a commercial surveillance backdoor distributed by an Italian company known as Hacking Team. The report also describes the potential involvement of vulnerabilities sold by the French company, VUPEN.
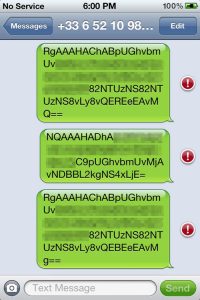
This report, written and coordinated by Citizen Lab Technical Advisor Morgan Marquis-Boire, analyzes several samples we believe to be mobile variants of the FinFisher Spy Kit targeting iPhone, Android, Blackberry, Windows Mobile and Symbian platforms. It is a follow-on to a previous research brief, From Bahrain with Love: FinFisher's Spy Kit Exposed?, that analyzed several pieces of malware targeting Bahraini dissidents.
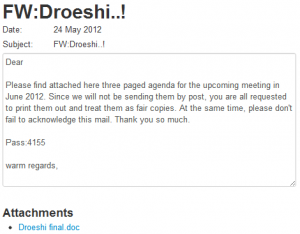
The Citizen Lab has analyzed recent targeted malware attacks against Tibetan organizations that share a common payload — LURK malware — and command-and-control server, as well as several other features.