Publications
Over the course of our multi-year investigation, we found that Dark Basin likely conducted commercial espionage on behalf of their clients against opponents involved in high profile public events, criminal cases, financial transactions, news stories, and advocacy. This report highlights several clusters of targets.
This campaign is the first documented case of one-click mobile exploits used to target Tibetan groups, and reflects an escalation in the sophistication of digital espionage threats targeting the community.
Documents stolen from a prominent journalist and critic of the Russian government were manipulated and then released as a “leak” to discredit domestic and foreign critics of the government. We call this technique “tainted leaks.”
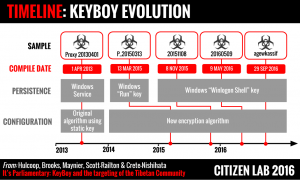
In this report we track a malware operation targeting members of the Tibetan Parliament that used known and patched exploits to deliver a custom backdoor known as KeyBoy. We analyze multiple versions of KeyBoy revealing a development cycle focused on avoiding basic antivirus detection.
This report describes a malware operation against the Syrian Opposition. We name the operator Group5, and suspect they have not been previously-reported. Group5 used “just enough” technical sophistication, combined with social engineering, to target computers and mobile phones with malware.