Publications
This annotated bibliography compiles and summarizes relevant literature on “digital transnational repression” (i.e., where states seek to exert pressure—using digital tools—on citizens living abroad in order to constrain, limit, or eliminate political or social action that threatens regime stability or social and cultural norms within the country). While transnational repression itself is not a new phenomenon, there has been limited research on how such repression is enabled and expanded by digital tools.
This submission outlines Canadian technology companies and the threat they pose to human rights abroad, as well as suggests mechanisms the Government of Canada’s RBC strategy can adopt to address the harmful impacts of Canadian-made technology.
Amidst calls for reform in Togo, NSO Group’s spyware was used to target voices for change including a bishop, priest, and opposition politicians.
Over the course of our multi-year investigation, we found that Dark Basin likely conducted commercial espionage on behalf of their clients against opponents involved in high profile public events, criminal cases, financial transactions, news stories, and advocacy. This report highlights several clusters of targets.
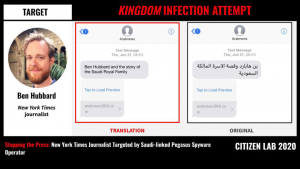
New York Times journalist Ben Hubbard was targeted with NSO Group’s Pegasus spyware via a June 2018 SMS message promising details about “Ben Hubbard and the story of the Saudi Royal Family.” The SMS contained a hyperlink to a website used by a Pegasus operator that we call KINGDOM. We have linked KINGDOM to Saudi Arabia. In 2018, KINGDOM also targeted Saudi dissidents including Omar Abdulaziz, Ghanem al-Masarir, and Yahya Assiri, as well as a staff member at Amnesty International.