NSO Group
In an investigative collaboration with Access Now, the Citizen Lab has analyzed forensic artifacts from the iPhone of award-winning exiled Russian investigative journalist Galina Timchenko and found with high confidence that on or around February 10th, 2023 it was infected with NSO Group’s Pegasus spyware.
While analyzing the phone of a Saudi activist infected with NSO Group’s Pegasus spyware, we discovered a zero-day zero-click exploit against iMessage. The exploit, which we call FORCEDENTRY, targets Apple’s image rendering library, and was effective against Apple iOS, MacOS and WatchOS devices.
We identified nine Bahraini activists whose iPhones were successfully hacked with NSO Group’s Pegasus spyware between June 2020 and February 2021. The hacked activists included three members of Waad (a secular Bahraini political society), three members of the Bahrain Center for Human Rights, two exiled Bahraini dissidents, and one member of Al Wefaq (a Shiite Bahraini political society).
Ron Deibert joins Al Jazeera to discuss the history of NSO Group’s Pegasus technology and why the expansive commercial spyware market deserves closer scrutiny and regulatory oversight.
Forbidden Stories and Amnesty International requested that the Citizen Lab undertake an independent peer review of a sample of their forensic evidence and their general forensic methodology. We were provided with iTunes backups of several devices and a separate methodology brief, and independently validated that Amnesty International’s forensic methodology correctly identified infections with NSO’s Pegasus spyware.
In its most recent response to the Citizen Lab regarding the The Great iPwn report, NSO Group extended an invitation to meet and discuss the Citizen Lab’s concerns and NSO Group’s “program” in more detail. We do not believe this invitation is made in good faith and have declined.
As highlighted by a coalition of human rights organizations in a letter to NSO Group released today, NSO Group continues to fail in human rights compliance. The company has fallen far short of numerous promises and commitments it made, in particular with regards to transparency and its human rights due diligence framework.
The Citizen Lab’s response to the questionnaire of the U.N. Working Group on the use of mercenaries on the provision of military and security products and services in cyber space by cyber mercenaries and related actors and its human rights impact.
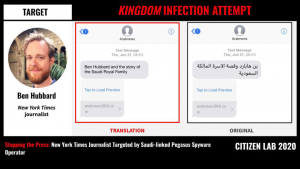
New York Times journalist Ben Hubbard was targeted with NSO Group’s Pegasus spyware via a June 2018 SMS message promising details about “Ben Hubbard and the story of the Saudi Royal Family.” The SMS contained a hyperlink to a website used by a Pegasus operator that we call KINGDOM. We have linked KINGDOM to Saudi Arabia. In 2018, KINGDOM also targeted Saudi dissidents including Omar Abdulaziz, Ghanem al-Masarir, and Yahya Assiri, as well as a staff member at Amnesty International.
This comprehensive Toronto Star profile provides an overview of the Citizen Lab’s work, impact, and history, mapping our journey from a initial Ford Foundation grant to an organization with 18 staff and a dozen research fellows.