NSO Group
Without Novalpina Capital—or the parties that you hired to conduct due diligence—concluding that Citizen Lab reporting is flawed and providing a substantiated basis to prove such a finding, it remains the case that you are purchasing a company implicated in serious human rights abuses and have decided to simply ignore this fact. It also remains the case that, without meaningful engagement with our research, your due diligence process will appear to many as nothing more than a superficial effort to check boxes and appease stakeholders concerned by NSO Group.
The purpose of this letter is to alert Jefferies Financial Group and lending firms interested in the syndicated loan to the Citizen Lab’s structured, evidence-based research into the abuse of NSO Group spyware, as well as investigations and research conducted by organizations such as Amnesty International, security companies, and the security team at Google Inc.
We appreciate your commitment—as stated in your letter of February 15, 2019—to “helping NSO Group become more transparent about its business.” As a first step, we ask that Novalpina Capital provide answers to the following questions regarding Novalpina Capital and NSO Group’s human rights due diligence and corporate social responsibility practices.
This report details how colleagues of a slain Mexican journalist investigating cartels were targeted with NSO Group’s Pegasus spyware in the days after his killing.
The Citizen Lab has sent an open letter to Francisco Partners in light of the apparent misuse of NSO Group’s technology– a company in which we believe Francisco Partners has a majority stake– and to request timely action in regards to issues raised in previous correspondence.
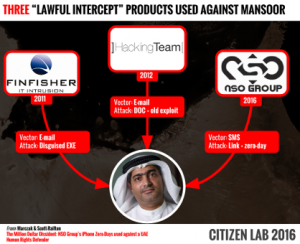
Citizen Lab senior research fellow Bill Marczak and Saudi dissident Omar Abdulaziz joined CNN to discuss how NSO’s Pegasus spyware found on Omar’s phone is linked to Jamal Khashoggi.
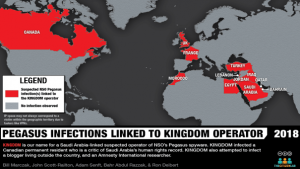
Following a Citizen Lab report that identified the presence of NSO’s Pegasus spyware technology in Quebec, researchers contacted Omar Abdulaziz, a Saudi Arabian dissident and Canadian permanent resident who has long been critical of the regime in Riyadh. After an extensive investigation, they discovered that his phone had been targeted with this powerful spyware and the operators of the technology were linked to Saudi Arabia’s government and security services.
In this report, we describe how Canadian permanent resident and Saudi dissident Omar Abdulaziz was targeted with a fake package delivery notification. We assess with high confidence that Abdulaziz’s phone was infected with NSO’s Pegasus spyware. We attribute this infection to a Pegasus operator linked to Saudi Arabia.
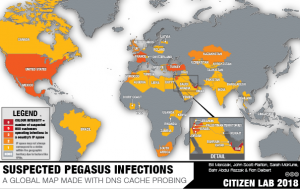
In this post, we develop new Internet scanning techniques to identify 45 countries in which operators of NSO Group’s Pegasus spyware may be conducting operations.
This letter requests a follow up to correspondence Citizen Lab sent to Francisco Partners in February after we discovered the apparent use of the products of its portfolio company, Sandvine, to surreptitiously inject malicious and dubious redirects for users in Turkey, Syria, and Egypt.