spyware
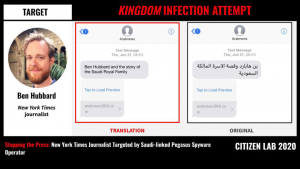
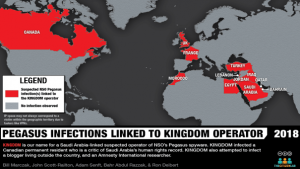
New York Times journalist Ben Hubbard was targeted with NSO Group’s Pegasus spyware via a June 2018 SMS message promising details about “Ben Hubbard and the story of the Saudi Royal Family.” The SMS contained a hyperlink to a website used by a Pegasus operator that we call KINGDOM. We have linked KINGDOM to Saudi Arabia. In 2018, KINGDOM also targeted Saudi dissidents including Omar Abdulaziz, Ghanem al-Masarir, and Yahya Assiri, as well as a staff member at Amnesty International.
This report provides an in-depth legal and policy analysis of technology-facilitated intimate partner surveillance (IPS) under Canadian law. Stalkerware apps are designed to facilitate remote surveillance of an individual’s mobile device use with the surveillance often being covert or advertised as such. Despite increasing recognition of the prevalence of technology-enabled intimate partner abuse and harassment, the legality of the creation, sale, and use of consumer-level spyware apps has not yet been closely considered by Canadian courts, legislators, or regulators.
This report was collaboratively written by researchers from computer science, political science, criminology, law, and journalism studies. As befits their expertise, the report is divided into several parts, with each focusing on specific aspects of the consumer spyware ecosystem, which includes: technical elements associated stalkerware applications, stalkerware companies’ marketing activities and public policies, and these companies’ compliance with Canadian federal commercial privacy legislation.
This research brief details how Griselda Triana, journalist and the wife of slain journalist Javier Valdez Cárdenas, was targeted with NSO Group’s Pegasus spyware in the days after his killing.
This report details how colleagues of a slain Mexican journalist investigating cartels were targeted with NSO Group’s Pegasus spyware in the days after his killing.
In this report, we describe how Canadian permanent resident and Saudi dissident Omar Abdulaziz was targeted with a fake package delivery notification. We assess with high confidence that Abdulaziz’s phone was infected with NSO’s Pegasus spyware. We attribute this infection to a Pegasus operator linked to Saudi Arabia.
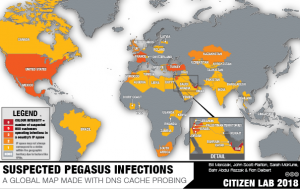
In this post, we develop new Internet scanning techniques to identify 45 countries in which operators of NSO Group’s Pegasus spyware may be conducting operations.
Citizen Lab validates Amnesty International investigation showing targeting of staff member and Saudi activist with NSO Group’s technology.
This report describes our investigation into the apparent use of Sandvine/Procera Networks Deep Packet Inspection (DPI) devices to deliver nation-state malware in Turkey and indirectly into Syria, and to covertly raise money through affiliate ads and cryptocurrency mining in Egypt.
On August 30, 2017 Citizen Lab’s Reckless V report received front page coverage on the New York Times. This report revealed that Claudio X. González, Director of a prominent anti-corruption organization, was targeted with government-exclusive spyware produced by the NSO Group. This is the latest in a growing case that reveals lawyers, journalists, human rights advocates, international […]