spyware
Claudio X. González, the director of Mexicanos Contra la Corrupción y la Impunidad (MCCI: Mexicans Against Impunity and Corruption), becomes the 22nd known individual abusively targeted with NSO’s spyware technology in Mexico.
Lawyers representing the families of three slain Mexican women were sent infection attempts with NSO Group’s Pegasus spyware after questioning official accounts of the killings.
The international investigation into the 2014 Iguala Mass Disappearance was targeted with infection attempts using spyware developed by the NSO group.
NSO Group’s Pegasus spyware and exploit framework were used in infection attempts against Mexican senators and senior politicians in June and July 2016.
Uncovering an operation using NSO Group’s Pegasus spyware and Trident exploit framework to target Mexican journalists, lawyers, and even a minor child.
This report describes an espionage operation using government-exclusive spyware to target Mexican government food scientists and two public health advocates.
This report describes a campaign of targeted spyware attacks carried out by a sophisticated operator, which we call Stealth Falcon. The attacks have been conducted from 2012 until the present, against Emirati journalists, activists, and dissidents.
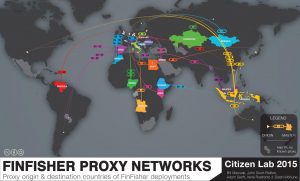
This post describes the results of Internet scanning we conducted to identify the users of FinFisher, a sophisticated and user-friendly spyware suite sold exclusively to governments.
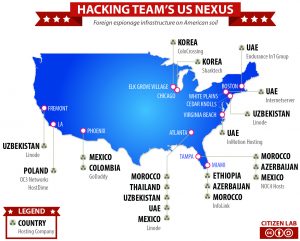
This report outlines an extensive US nexus for a network of servers forming part of the collection infrastructure of Hacking Team’s Remote Control System. The network, which includes data centers across the US, is used to obscure government clients of Hacking Team. It is used by at least 10 countries ranging from Azerbaijan and Uzbekistan to Korea, Poland and Ethiopia. In addition we highlight an intriguing US-only Hacking Team circuit.
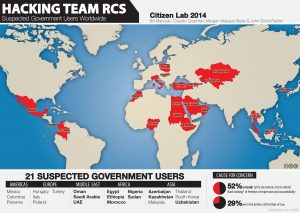
This post is the second in a series of posts that focus on the global proliferation and use of Hacking Team’s RCS spyware, which is sold exclusively to governments.