In this report, Citizen Lab Security Researcher Morgan Marquis-Boire describes analysis performed on malicious software used to compromise a high profile dissident residing in the United Arab Emirates. The findings indicate that the software is a commercial surveillance backdoor distributed by an Italian company known as Hacking Team. The report also describes the potential involvement of vulnerabilities sold by the French company, VUPEN.
Introduction
In July of this year, Morgan Marquis-Boire and Bill Marczak published analysis of what appeared to be FinSpy, a commercial trojan from the FinFisher suite of surveillance tools sold by Gamma Group International. Their report, From Bahrain with Love: FinFisher’s Spykit Exposed?, presented evidence consistent with the use of FinSpy to target Bahraini dissidents, both within Bahrain and abroad.
A range of other companies sell surveillance backdoors and vulnerabilities for what they describe as “lawful intercept tools.” Recently CSO magazine published an article reporting on claims by anti-virus company Dr Web that a backdoor known as “Crisis” or “DaVinci” was, in fact, the commercial surveillance tool “Remote Control System” sold by Milan, Italy-based lawful intercept vendor Hacking Team.1 According to an article published by Slate, the same backdoor was used to target Moroccan citizen journalist group Mamfakinch.2
This report examines the targeting of Mamfakinch and evidence suggesting that the same commercial surveillance toolkit described in these articles appears to have also been used in a recent campaign targeting Ahmed Mansoor, a human rights activist based in the United Arab Emirates (UAE). Additionally, it examines the possibility that a vulnerability linked to the French company VUPEN was used as the vector for intrusion into Ahmed Mansoor’s online presence.
The findings of this report contribute to a body of evidence of a growing commercial market for offensive computer network intrusion capabilities developed by companies in Western democratic countries. While the majority of these companies claim to sell their products to a restricted client base of law enforcement, military, and intelligence agencies, this report shows another example of commercial network intrusion tools being used against dissidents in countries with poor human rights records.
The market for commercial computer network intrusion capabilities has become a focus of controversy and debate about regulatory and legal controls that might be exercised over sales to such regimes or uses of the technology to target dissidents. Following the publication of From Bahrain with Love: FinFisher’s Spykit Exposed, the UK government reaffirmed that existing controls restricting the export of cryptographic systems apply to the Gamma Group’s exports of FinSpy.
In general, targeted malware attacks are an increasing problem for human rights groups, who can be particularly vulnerable to such attacks due to limited resources or lack of security awareness.
Recent Background: Da Vinci and Mamfakinch.com
On Friday the 13th of July 2012, the Moroccan citizen media and journalism project Mamfakinch3 was targeted by an electronic attack that used surveillance malware. Mamfakinch.com, a website that is frequently critical of the Moroccan government, received a message via their website directing recipients to a remote webpage:
The text, which hints at a sensitive scoop or lead translates roughly as “please don’t mention my name and don’t say anything at all [about me] I don’t want to get mixed up in this”.
The logs of the website reveal this message was sent from Moroccan IP space:
The IP from which the targeting message was uploaded (41.137.57.198) is from a Moroccan range dedicated to mobile 3G Internet users in the capital Rabat and its surroundings:
The page, found at http://freeme.eu5.org/scandale%20(2).doc prompted the user for the installation of malicious java, file, “adobe.jar”:
This file then facilitated the installation of a multi-platform (OSX and Windows) backdoor.
In the contents of the .jar you can see files called “win” and “mac” which correspond to Windows and OSX backdoors respectively:
The Windows backdoor contains a variety of clear-text strings which are found in the SSH-client, “Putty”. The OSX version of the backdoor, however, contains what appear to be to debug strings referencing the name of the developer, ‘Guido’:
Execution of the Windows backdoor writes the following files to disk:
The file ‘ZsROY7X.-MP’ appears to provide the main backdoor functionality:
It is executed via rundll32 and the following registry entry created to ensure persistence:
Processes such as iexexplorer.exe and wscntfy.exe are infected. Examination of loaded modules for “wscntfy.exe” reveals:
The backdoor has been identified as a variant of a commercial backdoor sold by the Italian Company “Hacking Team”. First identified by Russian Antivirus company Dr Web on July 25th, 2012, the backdoor has been called “Remote Control System,” “Crisis” and “DaVinci”.
The Hacking Team Remote Control System (RCS) is described in a leaked copy of their promotional literature as:
“A stealth, spyware-based system for attacking, infecting and monitoring computers and smartphones. Full intelligence on target users even for encrypted communications (Skype, PGP, secure web mail, etc.)”4
The Hacking Team public website stipulates that their technology is sold only to a restricted customer base:
“…we provide effective, easy-to-use offensive technology to the worldwide law enforcement and intelligence communities.”5
UAE Human Rights Activist Compromised
Ahmed Mansoor is a prominent UAE blogger and one of the ‘UAE Five’, a group of Emirati activists who were imprisoned from April to November 2011 on charges of insulting President Khalifa bin Zayed Al Nahyan, Vice President Mohammed bin Rashid Al Maktoum, and Crown Prince Mohammed bin Zayed Al Nahyan of the United Arab Emirates.6
On the 23rd of July, he received the following email (click image to enlarge):
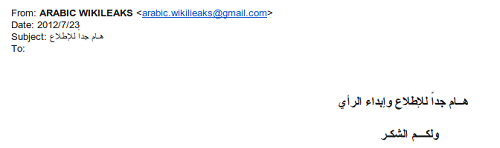
This email, sent from a suggestively titled e-mail address, urges the recipient to read a ‘very important message’ and it contained the following attachment:
The attachment is malicious. To the user it appears to be a Microsoft Word document, however it in fact is an RTF file containing an exploit which allows the execution of code that downloads surveillance malware.
This document exploits a stack-based buffer overflow in the RTF format that has been previously characterized:
“Stack-based buffer overflow in Microsoft Office XP SP3, Office 2003 SP3, Office 2007 SP2, Office 2010, Office 2004 and 2008 for Mac, Office for Mac 2011, and Open XML File Format Converter for Mac allows remote attackers to execute arbitrary code via crafted RTF data, aka “RTF Stack Buffer Overflow Vulnerability.”7
When Ahmed Mansoor opened the document, his suspicions were aroused due to garbled text displayed. His email account was later accessed from the following suspicious IPs:
Analysis of “veryimportant.doc”
The file “veryimportant.doc” is a downloader that downloads the second stage of the malware via HTTP:
Examination of the sample displays use of the windows API to download the 2nd stage (click image to enlarge):
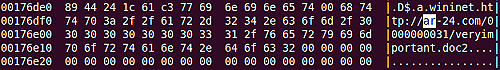
The 2nd stage is called “veryimportant.doc2”:
This is also a downloader that downloads the 3rd stage which appears to be the actual backdoor (click image to enlarge):
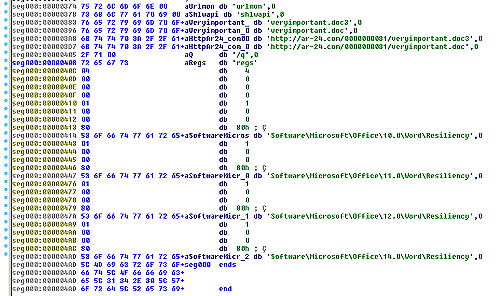
The executable code is downloaded from: http://ar-24.com/0000000031/veryimportant.doc3
Similar in behavior and appearance to the windows version of the RCS backdoor which targeted Mamfakinch, ‘veryimportant.doc3’ contains a variety of clear-text strings which are found in the SSH-client, “Putty”. On execution, “veryimportant.doc3” writes the following files to disk:
The following command is run, executing the file: “V46lMhsH.shv”
This then infects the following processes:
For example if we examine the process ‘wscntfy.exe” the following modules are loaded:
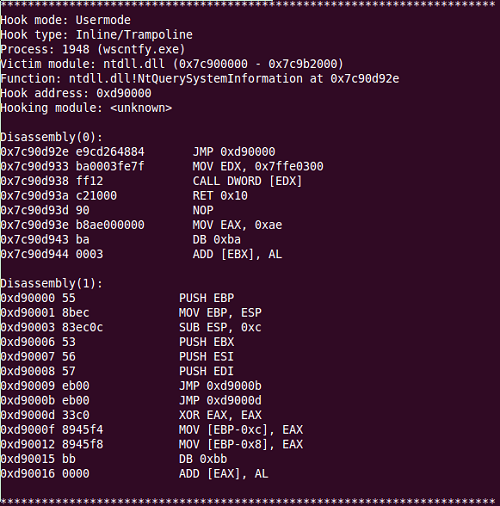
Examination of this process in the memory of an infected machine reveals the following functions are hooked by the malware:
We can see the malware infecting the process “wscntfy.exe”, visible in the memory region of the process which is marked as executable and writeable (click image to enlarge):
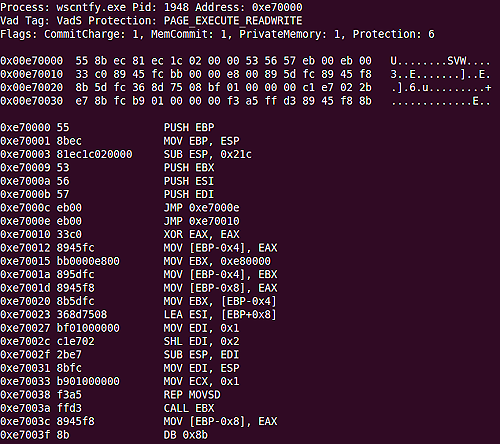
Here we see inline hooking of “NtQuerySystemInformation” performed by the malware, a technique frequently used to allow process hiding (click image to enlarge):
A registry key is added which ensures the persistence of the backdoor after reboot:
The file “V46lMhsH.shv” appears to perform the main backdoor functionality:
Further investigation of the implant reveals strings relating to popular anti-rootkit and anti-virus software, suggesting evasion of specific products:
We can also see the targeting of popular browsers:
And popular messaging clients:
The Windows implant includes a signed AMD64 driver. The certificate was issued by Verisign to “OPM Security Corporation”.
| CommonName: | OPM Security Corporation |
| Status: | Valid |
| Validity (GMT): | Mar 28, 2012 – Mar 28, 2015 |
| Class: | Digital ID Class 3 – Software Validation |
| Organization: | OPM Security Corporation |
| Organizational Unit: | Digital ID Class 3 – Microsoft Software Validation v2 Applications |
| State: | Panama |
| City/Location: | Panama |
| Country: | PA |
| Serial Number: | 21f33716e4db06fcf8641e0287e1e657 |
| Issuer Digest: | 4bc6f9b106c333db6c6a5b28e6738f7e |
OPM security appears to be a Panama based company:8
From their website:9
“From Panama to the World, OPM Security Corporation provides personal and institutional security tools and anonymity to you and your business.”
OPM Security is an OPM Corporation company.10 On their website, http://taxhaven.us, OPM Corporation states:
“O.P.M. CORPORATION, has been one of the leading providers of Offshore services since 1992 (check 266794). Through our headquarters in Panama, our Caporaso & Partners Law Office (check 25210) and correspondent offices in South America and Caribbean, we offer the best offshore packages.”
Command and Control
This malware calls back to the command and control domain: ar-24.com
This domain is registered through GoDaddy:
As of October 1st, 2012 this domain appears to be pointing to a Linode11 instance:
During August 2012, for a short period, this domain resolved to 83.111.56.188:
The physical address in the domain record (P.O. Box 5151, Abu Dhabi, UAE) matches the address for the corporate headquarters of Royal Group, which is a conglomerate of companies based in the UAE.
Identification
This malware contains the following strings:
The strings describing the Virtual Machine infection are the same as those described in the Symantec report on the Moroccan malware.
In addition to the similarities between the sample that Symantec and Dr. Web identified as being written by Hacking Team, “veryimportant.doc” is very structurally similar to this sample found on Virus Total.
This sample uses the following domain for command and control: rcs-demo.hackingteam.it
This information indicates that the sample matching “veryimportant.doc” may be a demo copy of the Hacking Team RCS backdoor. Promotional materials for this backdoor advertise the following features:12
The same promotional document mentions “Zero-day exploits” as a possible remote infection vector.
An additional sample with structural similarities to the 1st and 2nd stages was discovered in Virus Total.
This sample uses an exploit that has similarities in shellcode with “veryimportant.doc” however, the exploit it uses is newer, the Adobe Flash Player “Matrix3D” Integer Overflow.13 Searching for the origin of this exploit revealed a public mailing list post taking credit for discovery of this bug stating: “This vulnerability was discovered by Nicolas Joly of VUPEN Security”.
VUPEN are a French Security company who provide a variety of services including the sale of:
“…extremely sophisticated and government grade exploits specifically designed for offensive missions.”14
They claim to have discovered the vulnerability in January of this year at which point they shared this with their customers, prior to public disclosure in August:
The sample appears to have been created in May of 2012 prior to public disclosure:
While VUPEN take public credit for the discovery of this bug, it is possible that the exploit used here was not written by VUPEN but was independently discovered and weaponized by another party.
Recommendations
The use of social engineering and commercial surveillance software attacks against activists and dissidents is becoming more commonplace.
For at risk communities, gaining awareness of targeted threats and exercising good security practices when using email, Skype, or any other communication mechanism are essential. Users should be vigilant concerning all e-mails, attached web links, and files. In particular, carefully assess the authenticity of any such materials referencing sensitive subject matter, activities, or containing misspellings or unusual diction. If you believe that you are being targeted be especially cautious when downloading files over the Internet, even from links that are purportedly sent by friends.
For further tips on detecting potential malware attacks and preventing compromise, see Citizen Lab’s recommendations for defending against targeted attacks.
Acknowledgements
Malware analysis and report by Morgan Marquis-Boire.
Additional analysis by Andrew Lyons, Bill Marczak and Seth Hardy.
Additional Thanks
Thanks to Eva Galperin of the Electronic Frontier Foundation for activist outreach work with Mamfakinch.
Thanks to Chris Davis and The Secure Domain Foundation for malware and DNS information.
Additional thanks to John Scott-Railton.
Footnotes
1 http://hackingteam.it/
2 https://www.mamfakinch.com/
3 https://www.mamfakinch.com/
4 http://wikileaks.org/spyfiles/files/0/31_200810-ISS-PRG-HACKINGTEAM.pdf
5 http://hackingteam.it/index.php/about-us
6 https://en.wikipedia.org/wiki/UAE_Five
7 http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-3333
8 http://www.opmsecurity.com/security-tools/who-we-are.html
9 http://www.opmsecurity.com/
10 http://taxhavens.us/
11 https://www.linode.com/ – A company which provides virtual server hosting.
12 http://wikileaks.org/spyfiles/files/0/31_200810-ISS-PRG-HACKINGTEAM.pdf
13 http://www.securityfocus.com/archive/1/524143/30/60/threaded
14 http://www.vupen.com/english/

