Report
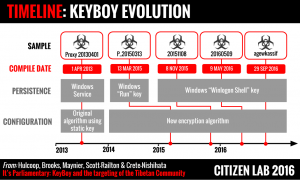
In this report we track a malware operation targeting members of the Tibetan Parliament that used known and patched exploits to deliver a custom backdoor known as KeyBoy. We analyze multiple versions of KeyBoy revealing a development cycle focused on avoiding basic antivirus detection.
In this report, we reverse engineer three popular live streaming platforms (YY, Sina Show, and 9158) and find keyword lists used to censor chat messages. Tracking changes to the keyword lists over the past year gives an inside look into how these applications implement censorship
In this post, we critically examine the Government of Canada’s proposal to indiscriminately access subscriber identity information that is possessed by telecommunications service providers. We conclude by arguing that the government has failed to justify its case for such access to the information.
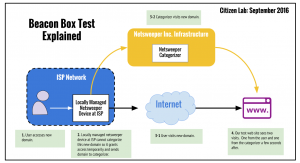
In this report, we confirm the use of the services of Canadian company Netsweeper, Inc. to censor access to the Internet in the Kingdom of Bahrain.
This report investigates the surveillance capabilities of IMSI Catchers, efforts by states to prevent information relating to IMSI Catchers from entering the public record, and the legal and policy frameworks that govern the use of these devices. The report principally focuses on Canadian agencies but, to do so, draws comparative examples from other jurisdictions. The report concludes with a series of recommended transparency and control mechanisms that are designed to properly contain the use of the devices and temper their more intrusive features.
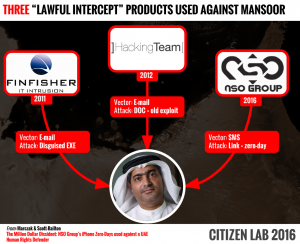
This report describes how a government targeted an internationally recognized human rights defender, Ahmed Mansoor, with the Trident, a chain of zero-day exploits designed to infect his iPhone with sophisticated commercial spyware.
In this report we analyze Windows and Android versions of web browser UC Browser, and find they transmitted personally identifiable information with easily decryptable encryption and were vulnerable to arbitrary code execution during software updates.
This report describes a malware operation against the Syrian Opposition. We name the operator Group5, and suspect they have not been previously-reported. Group5 used “just enough” technical sophistication, combined with social engineering, to target computers and mobile phones with malware.
This report describes a campaign of targeted spyware attacks carried out by a sophisticated operator, which we call Stealth Falcon. The attacks have been conducted from 2012 until the present, against Emirati journalists, activists, and dissidents.
In this research note, we analyze a malware campaign targeting Hong Kong democracy activists. Two new malware families are used in the campaign that we name UP007 and SLServer. Previous reports have shown overlap in the tactics, tools, and procedures used in this campaign in other operations targeting groups in Burma, Hong Kong, and the Tibetan community.