Report
In this post we examine how the Great Firewall of China is implementing DNS tampering and HTTP request filtering on KakaoTalk and LINE domains, which is disrupting service of the applications as a result. We find that Flickr and OneDrive are also blocked through DNS tampering. We also analyze recent changes to the LINE keyword filtering list.
Background & Key Findings The May 2014 coup d’etat in Thailand was the 19th coup attempt in the country’s history. It stands out from previous coups due to the military junta’s focus on information controls (defined below in more detail). It was also the first time that martial law was imposed before the coup, allowing […]
We analyze a newly discovered Android implant that we attribute to Hacking Team and highlight the political subtext of the bait content and attack context. In addition, we expose the functionality and architecture of Hacking Team’s Remote Control system and operator tradecraft in never-before published detail.
In this report, we document the results of network measurement tests we ran to determine how the Internet is being filtered in Iraq in reaction to ongoing insurgency in the country. The results identify 20 unique URLs that are blocked on three Iraq-based Internet Service Providers. Notably, none of the 7 websites we tested that are affiliated with, or supportive, of the jihadist insurgent group the Islamic State in Iraq and Greater Syria (ISIS) were found to be blocked.
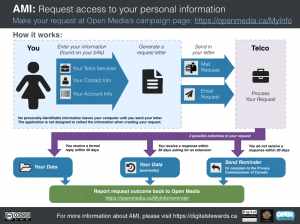
This post first identifies the individual and collective benefits of using the Access My Info tool to request access to one’s personal data held by Canadian data operators. It then discusses technical design decisions that went into the tool’s development and implementation.
This blog post investigates the recent blocking of video-sharing site Vimeo in Indonesia and examines the ongoing efforts to regulate online content in the country
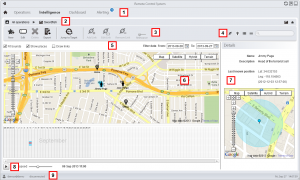
This report is the third in a series which analyzes regionally-based keyword censorship in LINE, a mobile messaging application developed by LINE Corporation. We document recent changes to the list of keywords used by LINE to trigger regionally-based keyword filtering for users with accounts registered to Chinese phone numbers.
In the past 24 hours The Citizen Lab has identified a maliciously repackaged copy of the popular circumvention software Psiphon 3. This post describes the malware and outlines steps to be taken.
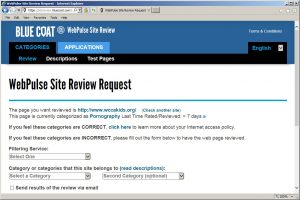
As a follow-up to our post about the number of sites miscategorized by SmartFilter, our tests with Blue Coat show that miscategorization is not a problem limited to a single product. We should be skeptical of any company’s claims that they are able to categorize much of the web accurately, or that their rate of “collateral damage” is very low.
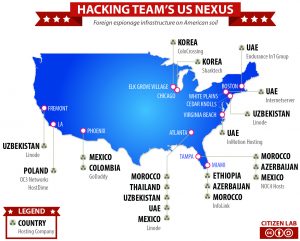
This report outlines an extensive US nexus for a network of servers forming part of the collection infrastructure of Hacking Team’s Remote Control System. The network, which includes data centers across the US, is used to obscure government clients of Hacking Team. It is used by at least 10 countries ranging from Azerbaijan and Uzbekistan to Korea, Poland and Ethiopia. In addition we highlight an intriguing US-only Hacking Team circuit.