Download PDF version I Read on ISSUU
Read the Arabic Version / النسخة العربية translated by Cyber Arabs
In this report, we document the results of network measurement tests we ran to determine how the Internet is being filtered in Iraq in reaction to ongoing insurgency in the country. The results identify 20 unique URLs that are blocked on three Iraq-based Internet Service Providers. These websites include social media platforms (such as Facebook and Twitter), proxy / circumvention tools (such as Psiphon), and the websites of mobile messaging apps (such as WhatsApp and Viber). Notably, none of the 7 websites we tested that are affiliated with, or supportive of, the jihadist insurgent group the Islamic State in Iraq and Greater Syria (ISIS) were found to be blocked.
Background
The ongoing insurgency within Iraq continues to escalate. In recent weeks, the jihadist group, the Islamic State in Iraq and Greater Syria (ISIS) seized control of the northern provincial capitals Mosul and Tikrit and Iraq’s largest oil refinery. The conflict has led Iraqi Prime Minister, Nouri al-Maliki, to formally request the U.S. military to engage in air strikes to limit the ISIS advances.
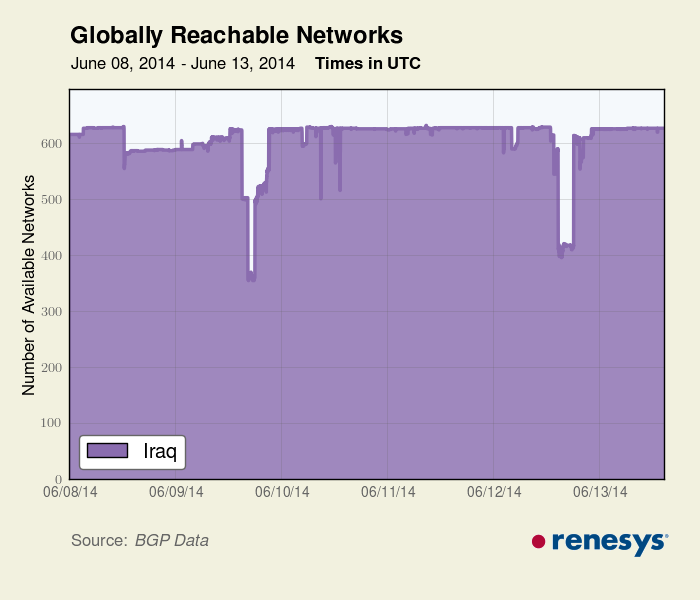
Following the seizure of Mosul and Tikrit, the government of Iraq implemented restrictions on Internet accessibility as means of limiting the ability of ISIS to mobilize and communicate their message. On June 13, 2014, reports emerged that numerous social media platforms, including Facebook, Twitter, and YouTube, had been blocked. By June 16, reports suggested that Ministry of Communications officials had ordered a complete Internet shutdown in certain regions. These reports are confirmed by BGP data from Renesys:
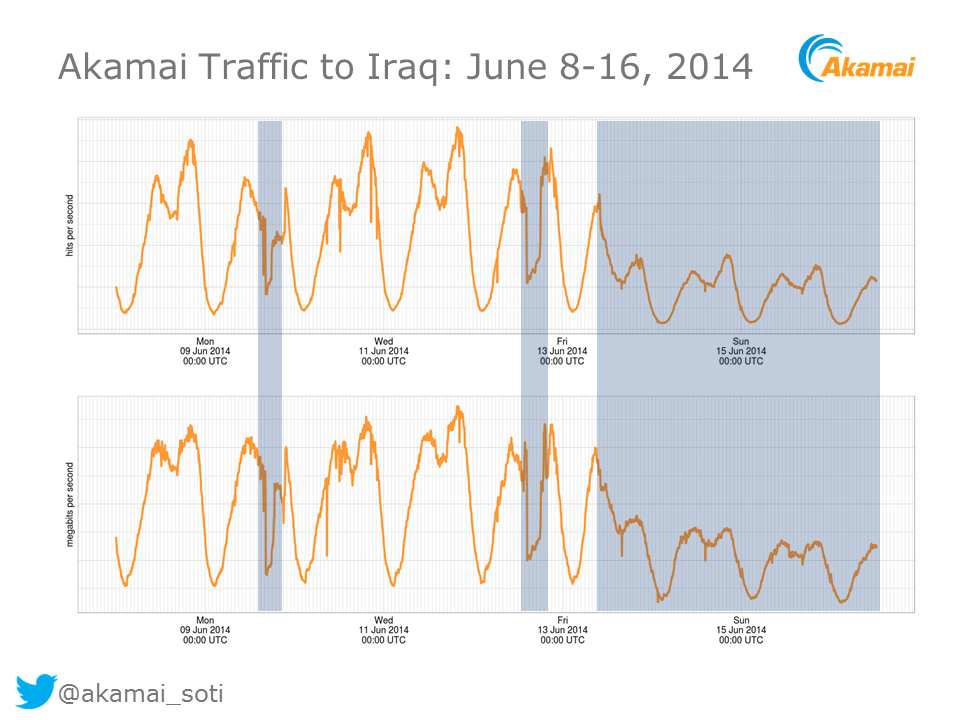
Similarly, traffic from the content delivery network Akamai dropped off substantially following the reported shutdown and blocks:
A letter allegedly leaked from the Ministry of Communications details these outages, indicating the ISIS-held provinces in which Internet access was to be blocked completely. In addition the letter lists websites and platforms (which included Facebook, Twitter, YouTube, Viber, Skype, and others) to be blocked.
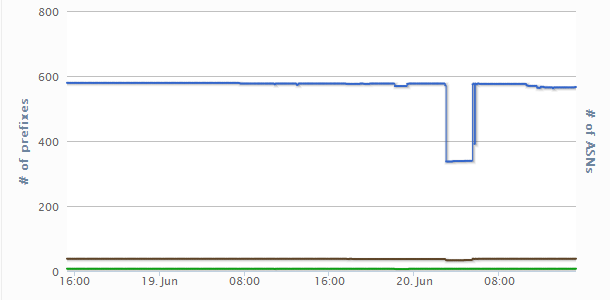
More recently, on the morning of June 20, measurements from the RIPE Network Coordination Centre showed 4 of the 38 networks in Iraq went offline, including Earthlink, as shown in Figure 3:
Renesys reported that these networks were restored several hours later:
ISIS actively uses social media to spread its messaging. For example, the group introduced an Android app in April 2014, called The Dawn of Glad Tidings, which leverages Twitter users’ accounts to share ISIS-related tweets. The application was removed from the Google Play store for violating community guidelines.
The group also uses well coordinated hashtag campaigns to spread their message, and had their Twitter account shut down after a number of graphic photos of victims attacked by ISIS were shared.
Complete shutdown of the Internet during political crises have been seen in numerous other countries in recent years, including Egypt and Libya during the 2011 Arab Spring and in Syria during the ongoing conflict in the country. We have documented the ways in which sensitive political events, ranging from violent conflict to elections and the hosting of international events, lead to changes in the application of information controls.
Methodology
We used two methods to determine if and how filtering is being applied in Iraq. The first method performs remote lookups of DNS records to identify suspicious results which could be indicative of filtering. The second method undertakes remote testing of website accessibility through proxies. We wrote a script that performs a GET request of a list of websites through six different publicly accessible proxies located in Iraq. We then compare the results of these GET requests with attempts to access the same URLs from the University of Toronto network to identify instances of blocking.
Early reports from Iraq suggested that blocking was performed on some ISPs through DNS tampering. DNS converts domain names (such as “citizenlab.org”) to an IP address (74.208.36.253). If the information in DNS records is tampered with, domain names can resolve to an incorrect IP address, which can lead visitors to a blockpage. In some cases, it is possible to perform lookups of the DNS records used by Iraq-based ISPs remotely, without being connected to that ISP directly. After performing these DNS lookups, we are able to compare the results for a given domain name with what we would expect to see to identify aberrations.
We performed a lookup of a list we compiled of 1,358 URLs to identify suspicious DNS results. We also did GET requests for the URLs on this list on the publicly accessible proxies we found in Iraq. This list contains content ranging from international news sites, social media platforms, and content specific to Iraq’s domestic political, social and cultural context. A full list of URLs tested can be found in the Data section.
Results
From June 16-20, 2014, we tested a list of 1,358 URLs remotely through eight name servers that correspond to the following ISPs:
| ISP | Hostname | IP address | Suspicious result? |
| IQ Net | nserver3.iqnet.com | 62.201.201.201 | Yes |
| IQ Net | nserver4.iqnet.com | 62.201.201.202 | Yes |
| Earthlink Telecommunications | n/a | 37.239.34.206 | Yes |
| Earthlink Telecommunications | n/a | 37.236.154.55 | Yes |
| ScopeSky | ns1.itc.iq | 185.23.153.242 | Yes |
| ScopeSky | ns2.itc.iq | 185.23.153.243 | Yes |
| Newroz Telecom | ns1.newroztelecom.com | 93.91.200.200 | No |
| Newroz Telecom | ns2.newroztelecom.com | 93.91.200.201 | No |
Earthlink Telecommunications
Remote tests of these nameservers showed a number of URLs resolved to the IP address 192.168.222.66, which is a private, non-routable IP address. See this example for a DNS lookup of psiphon.ca:
From our testing list, the following domains resolve to this IP address:
This result is unexpected. It is abnormal for a domain name to resolve to an IP address that is not publicly routable.
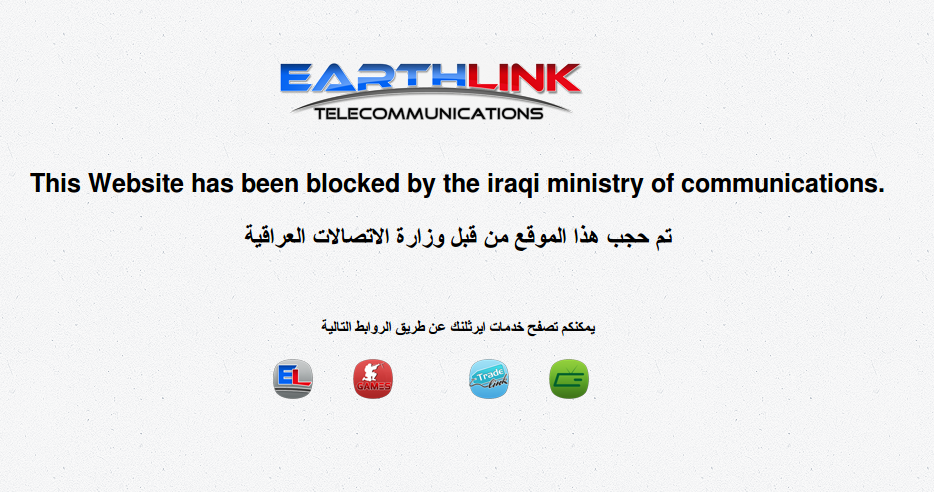
We tested the same list of sites through six Earthlink proxies from June 16 to 20, 2014. When accessing some sites we are redirected to the same IP address (192.168.222.66) and presented with the blockpage pictured in Figure 6.
Although there was some variability between sites found blocked on the six proxies, the following list of domains were found blocked at least once on one of the proxies, over the four day period.
In addition, when accessing this IP address (192.168.222.66) directly in a web browser, we also see the blockpage pictured in Figure 6.
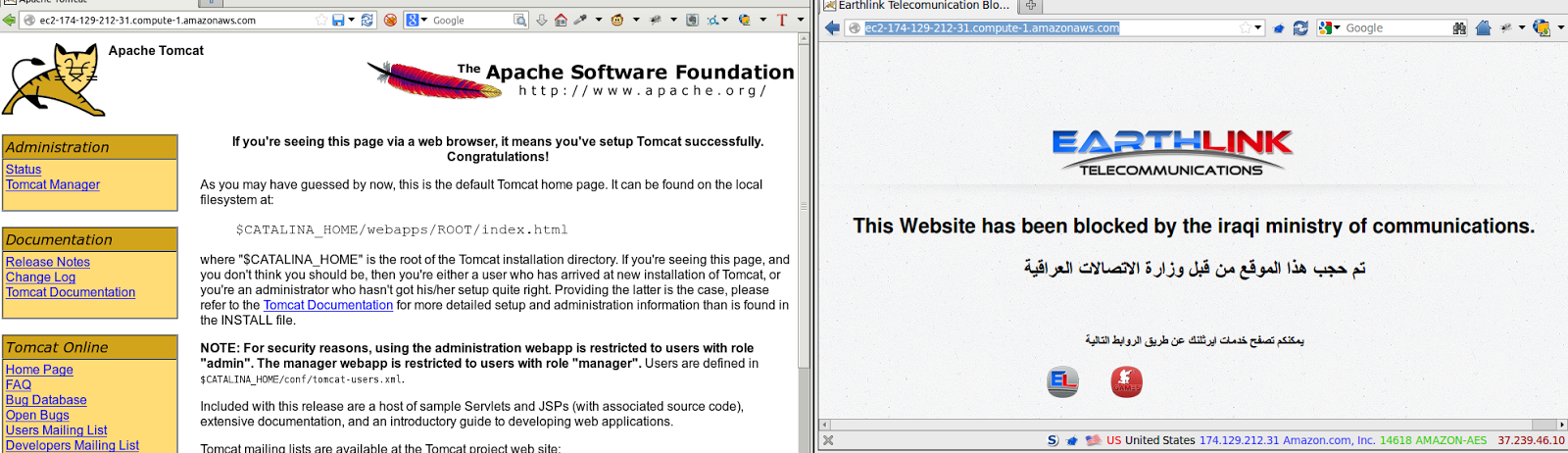
One interesting result is the block of the URL: ec2-174-129-26-64.compute-1.amazonaws.com. This domain naming scheme is consistent with servers hosted on the Amazon EC2 hosting service (a large and popular cloud hosting provider based in the United States). During subsequent testing we find that any domain in the *.compute-*.amazonaws.com domain namespace is blocked on this ISP. For example, this URL http://ec2-174-129-212-31.compute-1.amazonaws.com which is hosting no content other than the default placeholder content of a webserver is blocked on Earthlink:
Given that the content of this URL is benign it is likely not being targeted for blocking. This block is more likely to be the result of an overzealous filtering pattern used in the configuration of the domain name server.
This block also results in the collateral filtering of any URL that both hosts their website on the Amazon EC2 service and configures their DNS to use the compute-*.amazonaws.com domain, such as through a common name (CNAME) record. Examples of sites that are filtered as result of this configuration include:
http://www.virtuefitness.com/ – Fitness site
http://www.gayhealth.com/ – Defunct gay health information site
http://www.exoplatform.com/ – Social platform for companies
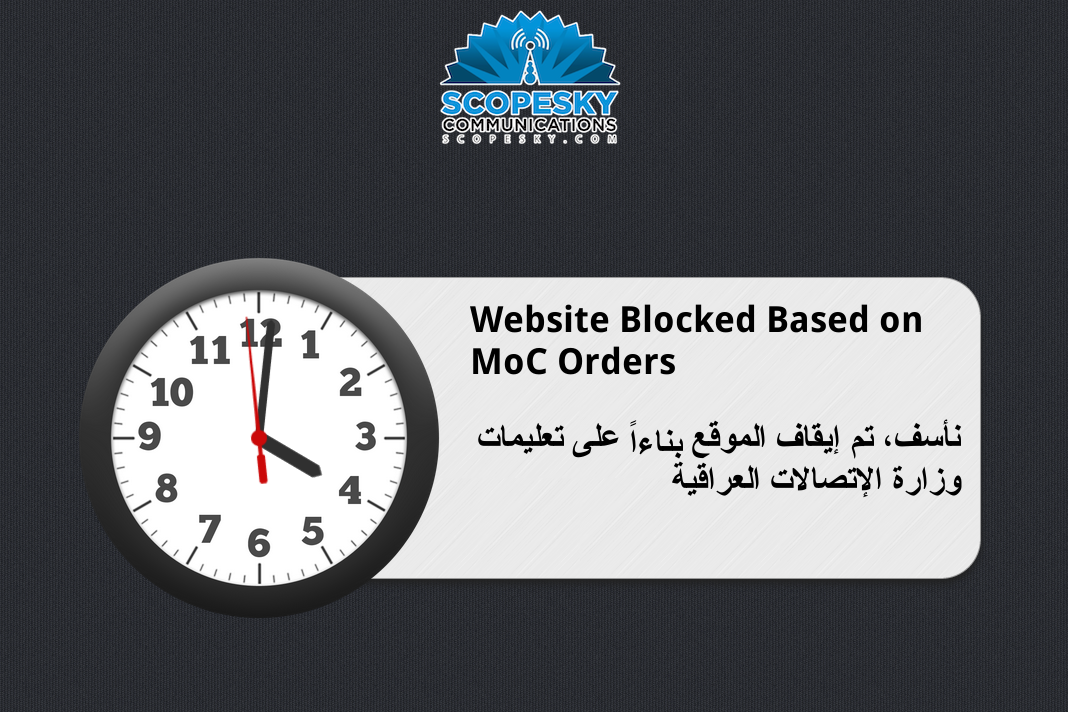
ScopeSky
From our testing list, five domains resolved to the IP address 185.23.153.235, as shown in this example of a lookup of twitter.com:
185.23.153.235 is an IP address hosted on the ISP ITC in Iraq:
When visiting this IP address in a web browser, we are presented with the following blockpage:
On this ISP the following domains were found to resolve to this IP address and are blocked:
IQ Net
During the course of testing our list through IQ Net, the nameserver gave responses that delegated the nameserver itself (nserver3.iqnet.com) as authoritative for a number of domains by altering the start of authority (SOA) record. See an example of this in a response for a DNS lookup for www.viber.com:
Compare this result to one using a public DNS resolver instead:
While this result is not itself evidence of deliberate filtering (for example, we may see such a result if a company such as Google were to host servers on the ISP), the list of domains with altered SOA is suspicious and is likely indicative of blocking. The following list of domains returned an altered SOA record when resolving through IQ Net name servers:
Newroz Telecom
There were no suspicious results found in tests of the nameservers of this ISP. This result was expected, because this ISP serves the Kurdistan area, and reports have indicated that the shutdown and social media blocking orders did not include Kurdistan.
Summary of results
The websites our tests found to be blocked represent a small number of content categories, and generally correspond with the list of sites ordered to be filtered by the Iraqi Ministry of Communications. We also tested the accessibility of 7 URLs of sites which are affiliated with or supportive of ISIS. We did not find any evidence, through both DNS lookups and proxy testing, that any of these URLs are blocked. Given that the insurgency was cited as the rationale for the shutdown and filtering, this finding is curious.
The following table summarizes the domains we found blocked in Iraq:
| Domain | Description |
| ec2-174-129-26-64.compute-1.amazonaws.com | Hosting Provider |
| hidemyass.com | Circumvention/Anonymization |
| instagram.com | Social media |
| www.softlayer.com | Hosting Provider |
| openvpn.net | Circumvention/Anonymization |
| plus.google.com | Social media |
| psiphon.ca | Circumvention/Anonymization |
| twitter.com | Social media |
| ultrasurf.us | Circumvention/Anonymization |
| www.dmoz.org | Web Portal |
| www.facebook.com | Social media |
| www.hotspotshield.com | Circumvention/Anonymization |
| www.skype.com | Voice-over-IP |
| www.strongvpn.com | Circumvention/Anonymization |
| www.tango.me | Mobile Messaging App |
| www.viber.com | Mobile Messaging App |
| www.whatsapp.com | Mobile Messaging App |
| www.xroxy.com | Circumvention/Anonymization |
| www.youtube.com | Video Sharing |
| www.wechat.com | Mobile Messaging App |
Circumvention usage in Iraq
In many cases Internet filtering implemented by DNS tampering is straightforward to circumvent. Users can simply select an alternate DNS service that will perform name resolution correctly. However this circumvention method can also be manipulated by censors, as seen recently in Turkey where providers intercepted requests to Google’s public DNS servers in order to prevent censorship circumvention. We have received anecdotal reports from users located in Iraq that using Google’s public DNS servers did not circumvent censorship, suggesting that DNS requests are being hijacked. However, circumvention services have reported increased usage from users based in Iraq.
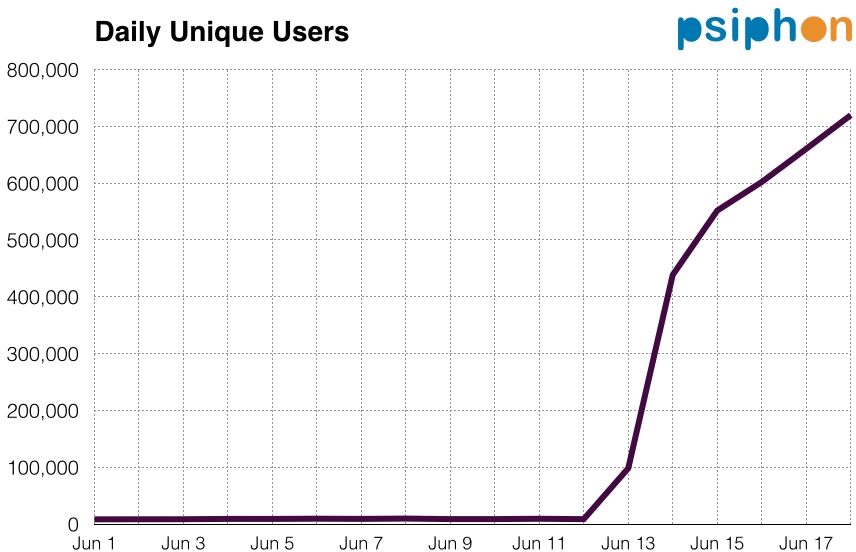
The circumvention service Psiphon reports a significant increase in users connecting from Iraq starting from June 13 after social media platforms were blocked, as seen in Figure 9. Note that 97% of these users are connected to Psiphon through their mobile phone using the Psiphon Android application.
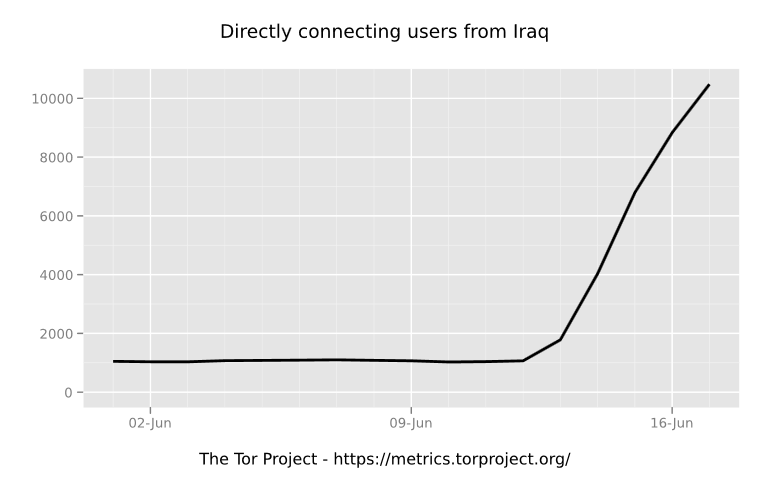
Similarly, usage of Tor, a popular anonymization tool which can circumvent censorship, has also increased significantly in June:
Conclusion
Given the volatile situation in the country, it is uncertain how Internet accessibility will be further affected. The Citizen Lab will continue to monitor the situation and post updates to our findings.
Data
A full list of data from these tests can be found at our GitHub repository.
Acknowledgements
Jakub Dalek, Adam Senft, Helmi Noman, and Masashi Crete-Nishihata undertook research and writing of this report, supported by the Social Sciences and Humanities Research Council (Canada) Grant 430-2014-00183, Prof. Ronald J. Deibert, Principal Investigator.
Media Coverage
Media coverage of the report includes VICE’s Motherboard and The Daily Beast.