Key findings
- The grocery chain Sobeys Inc. uses a system of “smart” in-store shopping carts developed by Caper. These carts allow customers to scan and pay for their purchases directly at their cart and receive a receipt via SMS or email.
- Electronic receipts issued by this system via SMS message share a URL that uses an easily predictable format. This system makes it possible to easily obtain the electronic receipts of other customers.
- These receipts contain a number of personal data points, including the customer’s partial credit/debit/Air Miles card numbers, a full list of purchases, and the date, time, and location of the customer’s purchase.
- We notified Caper and Sobeys of this concern. In response, Caper changed the format of the URL sent to customers who request an SMS receipt, but kept the old links accessible. Changing the format of the URL will make it more difficult for all receipts to be enumerated, however all URLs sent prior to this fix remain accessible and easy to enumerate. No response was received from Sobeys in response to either communication we sent them.
Overview
In 2019, the Canadian grocery chain Sobeys began using a system of “smart” shopping carts developed by the U.S.-based Caper.1 These carts allow customers to scan items as they place them in the cart, and use a series of visual and weight scanners to track the purchase of goods in the store. Customers are able to pay for their purchases using an interface on the shopping cart itself. Following the purchase, the customer is given an option to have their purchase receipt transmitted by SMS message or email.
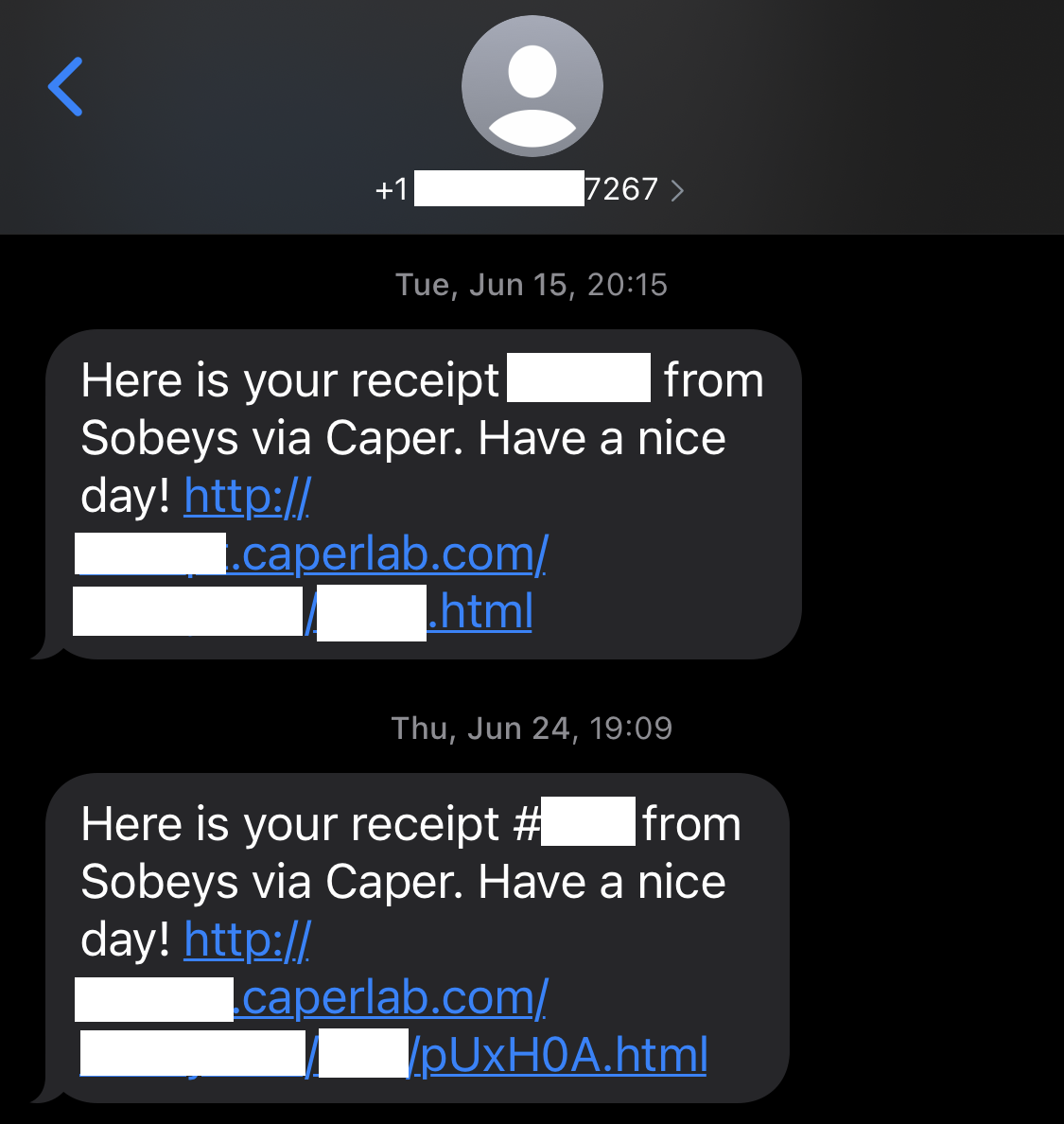
In June 2021, we used the Caper Cart system at a Sobeys location in Toronto, Ontario to make a purchase, and selected to receive an electronic receipt by SMS message. The SMS message sent contained a URL linking to a web version of the electronic receipt. That URL took the form:
http://[REDACTED_1].caperlab.com/[REDACTED_2]/12345.html2
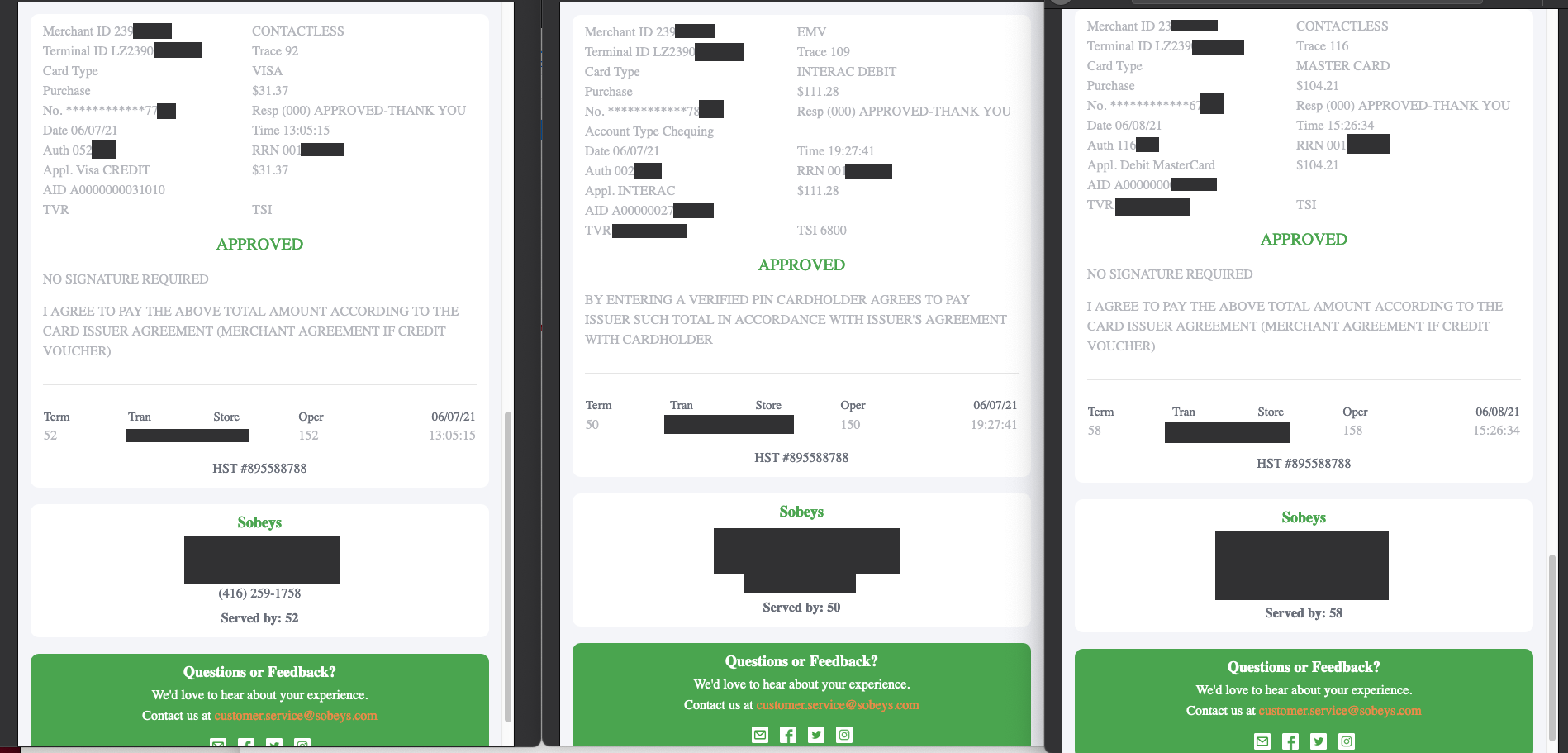
Clicking on this URL opened a web page containing the receipt. An example of such a receipt is shown in Figure 1:
However, we found that by incrementing the number contained in the receipt URL (for example, changing the “12345” value in our sample URL to “12346”), it was possible to access the receipts of other customers who had also shopped at this Sobeys location. We used this technique to access a small number of these receipts in order to confirm that this method was effective.
These e-receipts contain a number of personal data points, including the following information:
- A list of all items purchased and the purchase amount
- The last four digits of the credit or debit card used for the purchase
- The first and last three digits of the customer’s Air Miles card, if used
- The date, time, and location of the purchase
The sharing of private information in a manner that is easily accessible by guessing predictable receipt numbers represents a security risk to customers. We believe, but did not confirm, that we could easily access all customer receipts issued via SMS at this and other Sobeys locations.
While the credit, debit, and Air Miles card numbers were partially redacted, it is unlikely that two individuals would share the same partial card numbers. As a result, it would likely be possible to track the time and location of an individual’s purchases, as well as a full list of items purchased, across time.
Disclosure
The following table documents our communications to Sobeys and Caper regarding the disclosure of the issues we identified:
| Date | Contact |
|---|---|
| June 22, 2021 | We notified Sobeys and Caper of the issue we identified and described our organization’s policy on disclosing security vulnerabilities. |
| June 24, 2021 | A representative from Caper responded to our email about the issue. |
| June 29, 2021 | We spoke with a representative from Caper to discuss the issue. The Caper representative described the steps the company had taken to better protect URLs sent to customers from this point onwards. |
| July 26, 2021 | As we did not receive a response from Sobeys to our June 22, 2021 email, we sent a follow-up email reiterating our findings and intent to publish. No response was received from Sobeys in response to either communication we sent them. |
Table 1: Citizen Lab communications to Sobeys and Caper
Post-disclosure analysis
We visited the same Sobeys location on June 24, 2021 to duplicate our initial experiment. During this second experiment, the URL sent via SMS was in the following format:
http://[REDACTED_1].caperlab.com/[REDACTED_2]/[RECEIPT_NO]/[RANDOM].html
We believe that the use of a URL format that is not serialized and contains random values—and thus is not easily guessable—is a reasonable method of limiting the potential for all receipts to be enumerated.
On July 1st, we attempted to access the original e-receipts we collected in June 2021. We found that those links are still accessible. As of October 8th, 2021, the links are still accessible.
Conclusion
As companies collect, share, and store an ever-growing volume of personal data, it is imperative that they take steps to protect the security and privacy of this data.
The types of privacy and security concerns described here are not unique to any one retailer or technology vendor. They underscore the importance of companies having clear processes for security and privacy researchers to follow in order to report vulnerabilities. Caper responded to our disclosure and deployed a fix for the issue within 48 hours of our initial disclosure. As of the date of publication, we have not received a response from Sobeys.
Acknowledgments
Research undertaken in this report was supervised by Professor Ronald J. Deibert, principal investigator and director of the Citizen Lab.
- https://www.newswire.ca/news-releases/sobeys-pilots-smart-cart-the-first-intelligent-grocery-shopping-cart-803013190.html↩
- We have chosen to redact the specific URL shared in order to limit the potential for other receipts to be accessed. The URL displayed here shows the general form of the URL we received.↩