IGF 2013
Analyzing Content Controls in Indonesia (Part 2 of 4)
Figure 2: Ministry of Communication and Information Technology booth at IGF 2013 promoting Trust+ Positif
Building on past network measurements, legal, and policy analyses undertaken by the OpenNet Initiative, we set out to apply a mixed-methods approach to better understand the current situation in Indonesia. Our analysis is set in the context not only of the 2013 IGF, but amidst increasingly intense debates about free expression and access to information, and rapid technological change and development.
Islands of Control, Islands of Resistance: Monitoring the 2013 Indonesian IGF
Read the individual sections here:
- IGF 2013: Islands of Control, Islands of Resistance: Monitoring the 2013 Indonesian IGF (Foreword)
- IGF 2013: Monitoring Information Controls During the Bali IGF (Framing Post)
- IGF 2013: An Overview of Indonesian Internet Infrastructure and Governance (Part 1 of 4)
- IGF 2013: Analyzing Content Controls in Indonesia (Part 2 of 4)
- IGF 2013: Exploring Communications Surveillance in Indonesia (Part 3 of 4)
- IGF 2013: An Analysis of the 2013 IGF and the Future of Internet Governance in Indonesia (Part 4 of 4)
As we outlined in our framing post, information controls aim to manage the content accessible to a population, including information posted online. Content controls can include laws and regulations that restrict free speech online or in certain media, as well as technical measures designed to limit access to information — otherwise known as “Internet filtering.” We employ a multidisciplinary mixed-methods approach to study content controls that includes technical testing of government-mandated Internet censorship policies and practices, field research by regional and country-level experts, as well as analyzing the country’s legal and regulatory filtering framework. The combination of technical investigation with political, social, and legal contextual research is essential for understanding both how and why information controls are applied. We also aim to determine the specific techniques and, where possible, the products that are used to implement Internet content filtering.
Indonesia is a prime example of a country where mixed methods provide essential insight into the scope, scale, and character of content controls. As we described earlier, the country is characterized by a highly distributed and very competitive media environment in which Internet service providers (ISPs), civil society stakeholders, and government ministries engage in a sometimes contentious debate over what content should be filtered, by whom, under what processes, and according to which laws. The country has significant cultural and religious sensitivities around certain types of content. Although network measurement provides us with a baseline of data, our analysis of the scope, scale, and character of Indonesian content controls is greatly enriched by local knowledge of the Internet and cyberspace environment in the country, parts of which are explained in our infrastructure and governance post.
Building on past network measurements, as well as legal and policy analyses undertaken by the OpenNet Initiative, we set out to better understand the current situation. Our analysis is set in the context not only of the 2013 IGF, but amid increasingly intense debates about free expression and access to information, and rapid technological change and development.
While the detailed results of our analysis and technical tests are outlined below, our main findings can be summarized like this:
- Implementation of Internet filtering in Indonesia is decentralized (in both policy and technical processes). Although the Indonesian government sets broad expectations and “rules” (sometimes informally communicated) about what content should be filtered by ISPs, and is moving toward standardizing telecommunication laws that would more systematically regulate content control practices, the actual control of content today is left primarily to ISPs’ discretion.
- Reflecting the decentralized nature of the ISP environment, our research detected a range of Internet filtering devices and software, and a diversity of content-control practices being used on different ISPs. Some use the government-promoted systems DNS Nawala and Trust+ Positif, while others use different systems. For example, we found one ISP using Netsweeper, a content-filtering service manufactured by a Canadian company based in Guelph, Ontario.
- We also detected the presence of devices manufactured by California-based Blue Coat systems. We detected Packetshaper devices, which have the ability to monitor and control network traffic, on the two biggest Indonesian IPS, Telkom Indonesia and Indosat. We also found CacheFlow on Telkom Indonesia — an appliance whose primary function is to optimize bandwidth by caching but it can also be configured to block content.
- Although formally and officially, Indonesia requires pornography and gambling-related content to be blocked, we found that Indonesian ISPs apply content controls on content related not only to these areas of speech, but also to religious issues and religious advocacy groups, and content related to sexuality and gender (e.g., local LGBT community websites), among other content categories. We found that ISPs are inconsistent regarding the precise nature of content that they target for filtering.
- Citizens are prevented from accessing content that doesn’t fall within objectionable content on ISPs which rely on evidently error-prone mechanisms to categorize website URLs. We provide evidence that websites of academic institutions and government agencies are categorized on a Trust+ Positif URL list as “porn,” which results in these websites being blocked on ISPs relying on these URL lists.
- We ran network measurements on Internet connections provided at the 2013 IGF venue and found that the main network connection for workshop sessions was not filtered (as per the stipulations of the IGF host country agreement). However, backup connections (for public areas of the venue) provided by local Indonesian ISPs (Telkom and Indosat) did filter access to content. We compare these results with measurements from network vantage points outside of the IGF venue.
Legal and Regulatory Frameworks
Although Indonesia’s constitution guarantees freedom of expression under article 28E(3), a number of laws limit freedom of expression online and restrict access to content considered dangerous or socially unacceptable. The penal code and a 1965 blasphemy law that prohibits religious blasphemy are used to limit free expression. But the most prominent laws are the 2008 Electronic Information and Transaction (EIT) Law and the 2008 Anti-Pornography Law. Our blog post on infrastructure and governance explains the nature of these laws in greater detail.
The Electronic Information and Transaction Law limits freedom of expression and prohibits defamation. Free speech advocates requested a judicial review of the defamation article in the law, but the Constitutional Court denied the request in 2009. The Anti-Pornography Law was passed in October 2008 amid opposition from various groups who considered the law a threat to the cultural diversity and the rights of minority groups and women in Indonesia.
The Anti-Pornography Law, which was aggressively promoted and implemented by many ISPs and Internet cafés in 2010 in an effort to block millions of pornography sites during the holy month of Ramadan, was a major turning point for the country’s filtering policies and practices. At the time, efforts to build more centralized systems, such as DNS-Nawala and Trust+ Positif began to emerge with Indonesian policy-makers promoting their use among ISPs. Meanwhile, the government began installing Trust+ Positif on computers supplied to villages under its Desa Pintar (Smart Village) program. It was also during this period that the Indonesian government threatened to shut down BlackBerry in the country unless it began filtering pornographic content. BlackBerry announced in January 2011 that it would comply with the request and work with carriers to put a filtering solution in place.
Apart from specific invocations of the law, the Indonesian government also pressures ISPs to block websites it defines as extremist in nature. After religious violence erupted in the country in 2011, three hundred websites encouraging greater conflict were blocked as a consequence of this type of pressure. In July 2011, the ICT minister, Tifatul Sembiring, announced plans to filter websites offering illegal downloads of music and videos. He warned that users of these sites could face jail terms and heavy fines for illegal downloading. Individuals with intimate knowledge of these processes explain to us that requests to block content are occasionally passed on by government officials in phone calls or in person during meetings with ISPs and telecom employees. In other words, subtle pressures and moral suasion, rather than transparent and publicly accountable laws and regulations, are occasionally the means ministry officials employ to promote compliance.
As is the case in a number of other countries, Indonesian policy-makers have been using code words that create concerns of a growing interest in blocking access to or communication of content that is culturally, religiously, or politically offensive. For example, the INSAN Socialization Team of the Ministry of Communications and Information Technology (MCIT) has been actively promoting a “healthy and safe” Internet. The objective of the program is to “socialize a healthy and safe use of Internet to various levels of society in order to avoid misuse and take benefits for society.” Leading up to and during the 2013 IGF, Indonesian policy-makers emphasized the need to consider an “ethical” Internet — a euphemism around which some Indonesian civil society groups and IGF delegates, including the US State Department representative Christopher Painter, raised concerns.
Prosecution of Netizens
Indonesian laws, rules, and informal directions around content controls are reinforced by occasional prosecution of individuals. The following are some of the more egregious cases.
The most prominent case that invoked the Anti-Pornography Law involved pop singer Nazril Irham (also known as “Ariel”), whose homemade explicit videos were circulated on the Internet against his consent in June 2010. He was convicted and sentenced to three-and-a-half years in prison and a fine of USD 28,000, but he was released after serving only two-thirds of his prison sentence for good behaviour. Irham’s conviction, followed by other sex scandals involving local celebrities and politicians, prompted renewed calls for content control by the ICT minister, Tifatul Sembiring, to block access to pornography websites during the Ramadan in 2010. His teams immediately set out to deploy firewalls for more than 2,000 Internet cafés around the country, which he explained as a “race against time” to protect children from harm. Indonesia’s President Susilo Bambang Yudhoyono has also indicated his support for an Internet filter to block pornography.
One of the most prominent online defamation cases has been the prosecution of Prita Mulyasari, who was sued by the Omni International Hospital. Mulyasari, a Jakarta-based housewife and mother, communicated her disappointment with Omni Hospital’s service by e-mail to her friends in September 2008, which was forwarded, circulated on electronic mailing lists, and posted online. Once the e-mail became public knowledge, Omni International Hospital responded by filing a criminal complaint and a civil lawsuit against Mulyasari. She was then arrested in May 2009, by the Banten Provincial Prosecutor’s Office and charged under articles 310 and 311 of the penal code regarding defamation and article 27 of the EIT Law. The court had initially found Mulyasari liable in the civil case and ordered her to pay IDR 204 million (approximately USD 22,000) to Omni International. The charge sparked outrage among tens of thousands who joined a Facebook group in her support and held an online fundraising campaign called “Coins for Prita” to help her pay the fine. The campaign raised IDR 650 million or more than three times the amount of the fine. After appealing to the Supreme Court, she was later acquitted of all civil charges in September 2010. At the same time, criminal proceedings were underway, which eventually found her guilty. She was given a suspended sentence of six months’ imprisonment contingent upon good behaviour. Upon appealing in 2012, the Supreme Court overturned the lower court’s decision and quashed the criminal charges.
In June 2012, civil servant Alexander Aan was sentenced by a West Sumatra court to two-and-a-half years in prison and fined IDR 100 million (USD 11,100) (or face another two months in prison) for comments considered blasphemous made on his Facebook account and Facebook fan page, titled Ateis Minang (Minang Atheist). Aan’s conviction was justified on the grounds that he had violated the blasphemy provisions of the penal code, as well as article 28 of the Electronic Information and Transaction Law by “spreading racial and religious hatred.”
Technical Implementation of Content Controls
Because the Internet environment in Indonesia is broadly distributed, the scope and depth of what content is actually filtered can vary between ISPs, leaving users with different Internet experiences depending on where they connect from. Some ISPs even still offer, on occasion, an entirely unfiltered Internet, although that is increasingly rare. We confirmed this variation in both manual and automated network measurements, made from inside and outside the country.
In spite of the decentralization, there are also growing tendencies of standardization, if not centralization. For example, a number of national-level systems have emerged that offer filtering services, promoted by the MCIT. ISPs are encouraged to connect to these services as a way to subcontract out the job of Internet filtering and to ensure that ISPs comply with government expectations. Additionally, ISPs have begun to purchase commercial filtering products developed outside of Indonesia, for example those made by Netsweeper and Blue Coat, whose services include categorizing and controlling access to content online, thus taking the burden of maintaining content controls away from ISP administrators. Should more ISPs use these types of services, the existing decentralized architecture of the ISP ecosystem could in practice tend toward a degree of standardized content targeted for filtering, though that is not yet the case today.
As part of its national program “Healthy and Safe Internet” the INSAN Socialization Team of the MCIT is endorsing two DNS filtering projects that include configurations and URL lists to standardize content filtering on Indonesian ISPs, Trust+ Positif and DNS Nawala. Currently, the use of these programs is optional. Because ISPs use a variety of filtering systems and techniques, they are inconsistent regarding what content is blocked. During the IGF 2013 meeting, MCIT booths prominently displayed advertisements for and distributed materials about the “Healthy and Safe Internet” program that promotes Trust+ Positif and DNS Nawala (see Figure 1).

DNS-enabled Filtering Initiatives
Private sector associations in Indonesia have made several attempts to standardize content to be filtered and techniques for DNS filtering. Beginning in 2008, the Association of Indonesia’s Internet Cafés (AWARI) started an initiative to standardize filtering across Internet cafés and provide a means for users to report sites for blocking. Prior to 2008, filtering in Internet cafés was decentralized. Standardization of filtering was seen as positive development to ensure that Internet cafés operated on an equal footing.
These moves toward standardization were further enhanced with the development of DNS Nawala, an initiative that the MCIT started in November 2009 with the support of AWARI, PT Telkom, and Indonesian political parties in a response to pressures to implement the 2008 Anti-Pornography Law and the introduction of the “Healthy and Safe Internet” (INSAN) program. Standardization of content filtering was seen as a requirement to ensure compliance with the INSAN program. When DNS Nawala was launched, PT Telkom, the largest ISP in Indonesia, agreed to use the program. When PT Telkom announced it would use DNS Nawala, Eddy Kurina (vice president, public and marketing communication) stated that “for the growth and development and improvement of quality of young generation and as part of the Corporate Social Responsibility program, Telkom provides DNS Nawala able to select the internet contents.” The program was set back when network disruptions followed an installation of DNS Nawala on a major Internet Exchange Point.
The Indonesian Internet Service Provider Association (Asosiasi Penyelenggara Jasa Internet Indonesia, APJII) has an agreement with DNS Nawala to provide the 250 members of the ISP association with use of the service. As part of this cooperation APJII provides DNS Nalawa with five servers and DNS Nawla in turn gives its block lists to APJII members.
The use of DNS Nawala is not compulsory for APJII members. However, in a statement APJII Chairman Sammy Pangerapan cautioned APJII members that they are responsible for content on their networks and the APJII encourages members to use the service.
Trust+ Positif
Trust+ Positif is maintained and endorsed by the MCIT, and provides content-filtering capabilities distributed as configuration files and block lists for the popular open source Squid HTTP proxy and the SquidGuard add-on which is an open source implementation of URL access control lists for Squid. Trust+ Positif is another attempt to standardize content filtering in Indonesia and is described as providing access to a “safe and healthy internet by protecting Internet access based on series of lists containing healthy and reliable information.” The system aims to protect society against values, ethics, and morals “that do not fit with the image of the Indonesian nation.”

Trust+ Positif feeds SquidGuard two URL databases:
- Domain List — contains a list of top-level domains. If a domain is found on this list (e.g., facebook.com) then any subdomain or path (e.g., *.facebook.com or www.facebook.com/home.php) which includes the top-level domain will be included.
- URL List — contains lists of single URLs (e.g., www.facebook.com/pages/Everybody-Draw-Mohammed-Day).
These lists group URLs and domains into a number of categories:
- White List (positive/reliable) — This category includes domains and URLs that have been flagged as “positive or trusted” (e.g., government domains).
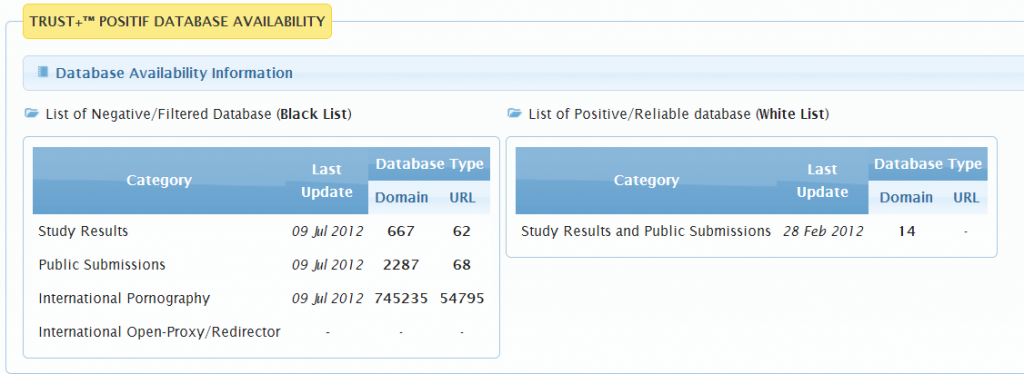
- Black List (negative/filtered) — This category contains URLs and domains with content considered “negative” such as pornography. The black list is divided into three categories: “Study Results and Public Submissions,” “International Pornography,” and “International Open-Proxy.”
The content of these lists and information about the number of domains and URLs included are made publicly accessible, as Figure 3 illustrates.
The Trust+ Positif website includes a submission page that encourages users to participate in the development of URL lists (to blacklist websites for filtering or whitelist for accessibility) by forwarding pages to an e-mail address or filling in a submission form (at the time of publication, this form is described as “under development”). However, how this submission process operates in practice is unclear and the MCIT ultimately decides what to block. No judicial order is required.
Trust+ Positif URL Miscategorization
The Trust+ Positif website provides users with the option to search for information about domain names or URLs that have been registered in the Trust+ Positif URL lists. This search helps users find out whether a domain name or URL has been listed in the Trust+ Positif database, and check for its categorization.
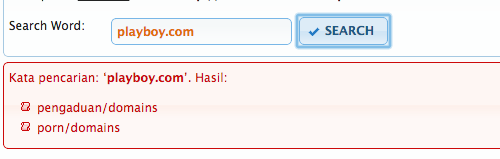
We entered URLs of websites containing sexual and pornographic content and the database returned their categorization as “porn” websites. For example, the URL www.playboy.com was returned as “porn,” as Figure 4 shows.
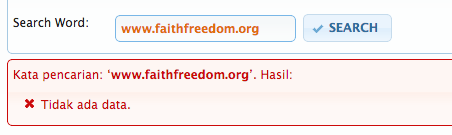
However, when we tried URLs of nonpornographic websites that have been found blocked on some Indonesian ISPs, the database returned no data. For example, a search for the website www.faithfreedom.org, which has alternative views on the faith of Islam, returned the message “Tidak ada data” (no data), as can be seen in Figure 5.
We analyzed how the Trust+ Positif URL dataset categorizes a sample of URLs and found that there are numerous URL miscategorizations that result in erroneous blocking. We downloaded the block list that categorizes which domains are pornographic — it is publicly available on the Trust+ Positif website. We then searched through the list to find examples of potential miscategorizing. Once completed, we verified that these URLs and domains are currently in the Trust+ Positif URL lists by submitting them to their online URL-checking tool.
Examples of such miscategorization are provided in Table 1.
| URL | Content | Categorization in the Trust+ Positif Database |
|---|---|---|
| glbtss.colostate.edu | GLBT Resource Center at Colorado State University | Porn |
| www.muslimsconnect.com | Dating website | Porn |
| gibraltar.gov.uk | UK government website about Gibraltar | Porn |
| www.newspiritchurch.org | New Spirit Community Church | Porn |
| www.libertyeducationforum.org | Liberty Education Forum – Think tank from Washington, DC | Porn |
| www.civilmarriagecivilright.com | LBGT social issues and personal site | Porn |
| www.equalityforum.com | LGBT social issues site | Porn |
| wcl.american.edu/journal/lawrev/49/vol49-5rothenberg.pdf | Academic paper about peeping Toms | Porn (urls) |
| lib.rochester.edu | Library at the University of Rochester | Porn |
| www.slowtrains.com | Literary journal | Porn |
| www.eastcoastcomputers.com | IT firm from Florida | Porn |
| www.lavalife.com | Dating site | Porn |
Examples of URLs miscategorized in the Trust+ Positif database as “porn”
Alexa ranks the Trust+ Positif website served to users who browse blocked content on certain ISPs (www.internet-positif.org) among the top hundred pages accessed in Indonesia (number 72 on 24 October 2013) which suggests that a significant number of access attempts are served the block page.
Comparison of DNS Nawala and Trust+ Positif Block Lists
We compared both DNS Nawala and Trust+ Positif lists of domains that they categorize as pornographic content. The DNS Nawala block list was retrieved at a time in which a misconfiguration of the DNS Nawala website in 2010 allowed for the download of the block list. The Trust+ Positif blocklist was retrieved directly from a public link on their website. We found that the majority of domains listed are common between the two sets of lists. The Trust+ Positif list does not include any additional domains that are included in the DNS Nawala list, while the DNS Nawala list has 205 additional domains that are not in the Trust+ Positif list.
Canadian and US Commercial URL filtering Products Detected in Indonesia
Netsweeper
Netsweeper is a technology company based in Guelph, Ontario, that provides software products used to filter Web content. In previous research, we found that Netsweeper software was deployed to censor political and human-rights-related content at the national level in Pakistan, Qatar, Kuwait, UAE, and Yemen. We searched for signatures of the Netsweeper products in the search engine Shodan, using methods described here, and we found an installation of Netsweeper on the Indonesian ISP PT Excelcomindo Pratama.
The Netsweeper control panel appears at http://202.152.254.227:8080/webadmin/start, while the block page is accessible at http://202.152.254.227:8080/webadmin/deny/index.php.
Blue Coat
Blue Coat Systems is a California-based provider of network security and optimization appliances. Some of these products can enable network filtering and surveillance. These products include: ProxySG which works with WebFilter, to categorize web pages for filtering; PacketShaper, a cloud-based networking management device that can establish visibility of over six hundred web applications and control undesirable traffic; and CacheFlow, a web-caching appliance that optimizes bandwidth. ProxySG provides “SSL Inspection” services to solve “issues with intercepting SSL for your end-users.” PacketShaper has the ability to monitor and control network traffic: it is integrated with WebPulse, Blue Coat Systems’ real-time network intelligence service that can filter application traffic by content category. CacheFlow can be configured to block content.
While these tools can be used to maintain and secure networks, they can also be used to implement politically motivated restrictions on access to information, and monitor and record private communications. Depending on their end use, these tools can be used to serve legitimate and positive purposes, or purposes resulting in adverse impacts on human rights. This capacity is often referred to as “dual-use,” a term adapted from language used to describe technologies with both civilian and military applications.
As part of prior Citizen Lab research that included a combination of wide-area scanning techniques, Shodan queries, and other experimental methods, we found Blue Coat devices on public networks in eighty-three countries (twenty countries with both ProxySG and PacketShaper, fifty-six countries with PacketShaper only, and seven countries with ProxySG only). Among those findings was the presence of PacketShaper on the networks of both Indosat (http://202.155.63.62/login.htm) and Telkom Indonesia (http://203.130.193.156/login.htm) networks. We also found installations of CacheFlow on Telkom (http://180.252.181.1).
Network Measurements
We used a variety of techniques for measuring censorship on networks in Indonesia, including client-based tests performed within Indonesia and remote tests through publicly available web proxies and virtual private networks (VPNs).
Client-based tests: Data were collected by performing synchronized HTTP requests in both a field location (i.e., a location where Web censorship is suspected) and lab location (at the University of Toronto) using customized measurement software written in Python in a client-server model. The lab network acts as a control and is located at a site that does not censor the type of content tested by the measurement software. The field locations included a number of Indonesian ISPs.
During tests the client attempts to access a pre-defined list of URLs simultaneously in the country of interest (the “field”) and in a control network (the “lab”). Tests were conducted on URL lists that consisted of globally sensitive URLs, tested in all regions, and locally sensitive URLs that are specific to Indonesia’s social, political, and cultural context.
A number of data points are collected for each URL access attempt: HTTP headers and status code, IP address, page body, and in some cases traceroutes and packet captures. A combined process of automated and manual analysis attempts to identify differences in the results returned between the field and the lab to isolate instances of filtering. Because attempts to access websites from different geographic locations can return different data points for innocuous reasons (such as a domain resolving to different IP addresses for load balancing, or displaying content in different languages depending on where a request originates from) a manual inspection of results is often necessary to verify whether inaccessibility is caused by deliberate filtering or mundane network errors.
In addition to tests using our measurement software, tests were also run with two other network measurement tools: Netalyzr and OONI-Probe. Netalyzr is a network diagnostic tool developed at the University of California, Berkeley. We ran it to gather additional data about the properties of tested networks. Collin Anderson, an independent researcher who attended the 2013 IGF, also ran tests with OONI-probe (a client-based Internet censorship measurement tool developed by the Tor project) and contributed his results to this post.
Remote tests: We ran tests of website accessibility using publicly available Indonesian web proxies and VPNs. The purpose of these tests was to help develop our URL-testing lists for client-based measurements.
2008-2010 Network Measurement Results
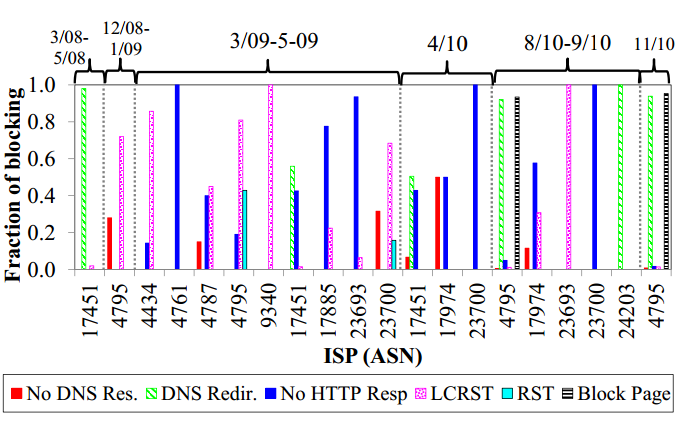
Between 2008 and 2010 we ran client-based network measurements on twenty different ISPs in Indonesia. The results of this testing show significant decentralization in how Indonesian ISPs technically implement filtering; they also show inconsistency between ISPs in terms of what content is blocked.
On Indosat (AS 4795) and XL Axiata (AS 24203) we observed block pages delivered via DNS redirection to IP addresses hosted by each ISP, and we noted that Indosat’s use of block pages began in late 2010. Similarly, we observed XL Axiata implementing a combination of DNS redirection and block pages in 2010, but we lacked longitudinal data about this ISP.
In contrast to Indosat and XL Axiata that display block pages, BIZ Net (AS 17451) implemented DNS redirects that went to non-routable IPs that therefore look like transient failures from the user’s perspective. In 2008, redirects went to IP 0.0.0.1, but in 2009 and onwards we saw this shift to the link-local IP 169.254.1.1 address. Finally, in sixteen different tests over three years, First Media (AS 23700) showed no evidence at all of DNS redirection.
The specific content blocked is also inconsistent across ISPs. Pornographic content and gambling websites were regularly blocked by Indonesian ISPs in our sample. However, testing conducted from 2009 to 2010 showed that on some ISPs (e.g., Indosat, XL Axiata) blocked websites included content related to free expression (e.g., www.freespeech.org, an online video network, and www.freespeechcoalition.com, a free speech group), as well as anonymizers and censorship circumvention software. Content related to local LGBT community groups and information portals was also found blocked.
A summary of historical data that ONI has collected from Indonesia from 2008 to 2010 appears in Figure 7. It shows the ration of blocking behaviours observed on different ISPs in the region. The possible behaviours indicated are:
- No DNS response — when there is no DNS response given in Indonesia, while there is a response in Toronto
- DNS redirection — when a DNS query redirects to a different IP in Indonesia compared to a DNS query from Toronto
- No HTTP response — when an HTTP response is seen in Toronto but not in Indonesia
- LCRST (low confidence reset) — when the page is retrieved successfully in Toronto (Response code < 400) while a reset packet is observed in Indonesia with no content returning
- RST (reset) — when LCRST occurs more than three times in a week for the URL in Indonesia
- Block page — when a known block page is returned in Indonesia.
2013 Network Measurement Results
Remote Measurement Results
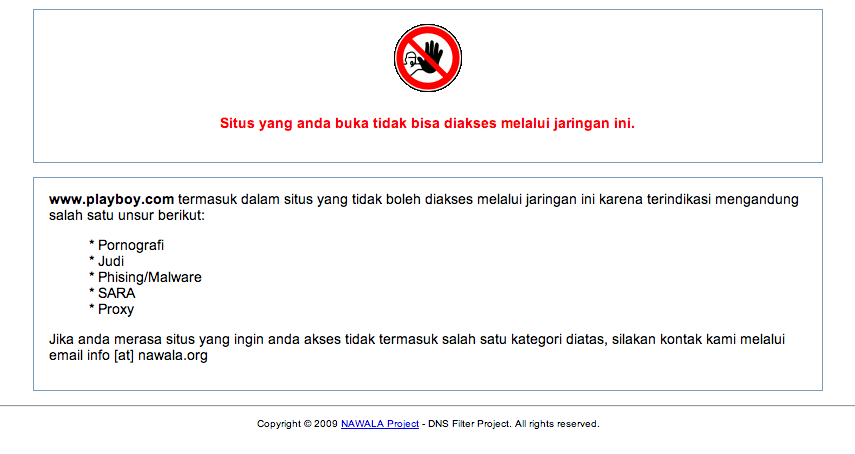
Nawala: Testing was conducted using Nawala’s publicly accessible DNS servers (180.131.144.144 and 180.131.145.145) using the same list of URLs used for in-country testing. Two hundred and fifteen URLs from this list of 1,387 URLs resolved to the IP address 180.131.146.7, which is the block page for the Nawala service shown in Figure 8. The full list of URLs tested and found blocked using the Nawala service can be found here.
The block page reads (translation from Indonesian):
The website you are trying to open cannot be accessed on this network. www.playboy.com is categorized as one of the following:
- Porn
- Gambling
- Phising [sic] /malware
- SARA [SARA stands for “Suku, Agama, Ras, Antar-golongan,” which refers to content related to ethnicity, religion, race, and intergroup relations].
If you feel the website that you want to access is erroneously categorized, please contact us via email [email protected]
Client-based Measurement Results
Client-based network measurements were run on four ISPs, including three connections provided to delegates at the IGF 2013 venue and one ISP outside of the IGF venue to provide a basis for comparison between content controls at the IGF and those elsewhere in the country.
ISP: TRI
AS: THREE-AS-ID Hutchison CP Telecommunications, PT
Netalyzr Results
Testing was conducted on 22 and 23 October 2013 on the ISP Tri using a 3G mobile connection tethered to a laptop running our client-based measurement software. Test results showed 142 URLs blocked out of the sample of 1,387 URLs we tested. Blocked content spanned twenty-two content categories, including LGBT content, critical religious content, independent media, circumvention tools, sex education sites, gambling, and pornography. A full list of blocked content can be found here.
Blocked content resolved to a private routable IP address of 10.70.25.111 and displayed a nontransparent block page stating “It works!” The HTML source is identical to the default web page of a fresh installation of the Apache Web server, as Figure 9 illustrates.

IGF Venue Network Measurement Results
The Bali Nusa Dua Convention Centre (the venue for the 2013 IGF) provided four wireless connections to participants (SSIDs: IGF 2013, IGF-a, IGF2013.wifi.id, IGF2013@Indosat). See Figure 10.

The host country agreement signed between the government of Indonesia and the United Nations mandates that an open Internet connection is provided. The primary wireless network, identified by the SSID IGF2013, intended to offer this unfettered access. A network administrator from the organizing committee informed us that “the main wi-fi access managed by [the IGF host] committee is using SSID IGF2013, and we didn’t filter any sites.” A 5 Ghz version of this primary network, with the SSID IGF2013-a, was also made available. Both of these connections rely on bandwidth from Telkomsei and are routed out of the country through that ISP. However, these connections have their own Network Operations Centre (NOC).
Two other networks were available at the event and are under the filtering regimes of their respective ISPs: [email protected] is provided by Telkomsei and IGF2013@Indosat is provided by Indosat. These ISPs are the two largest providers in Indonesia and regularly provide connectivity to the Bali Nusa Dua Convention Center where the 2013 IGF and other major events such as the recent 2013 APEC conference summit were held.
SSID: IGF2013 – IPV6 (2.4 GHgz)
AS: IGF2013-ID Internet Governance Forum 2013
Netalzyer Results
Testing on the SSID IGF2013 (AS: IGF2013-ID Internet Governance Forum 2013) showed no evidence of filtering out of the 1,387 URLs tested. Organizers described this network as offering unfettered access as per the UN host agreement, and our technical testing verified this claim.
SSID: [email protected]
AS: TELKOMNET-AS2-AP PT Telekomunikasi Indonesia
Netalyzer Results
Testing on the SSID [email protected] (AS TELKOMNET-AS2-AP PT) found 197 URLs blocked out of the sample of 1,387 URLs tested through DNS tampering. A variety of content was blocked, including LGBT content, independent media sites, critical religious content, and circumvention and anonymizer tools. A full list of blocked URLs can be found here.
All blocked content resolved to the IP address 118.98.97.100. Users were redirected to a block page hosted at www.internet-positif.org, like this response to an HTTP GET request:
HTTP/1.1 307
Server: nginx
Date: Mon, 21 Oct 2013 10:22:31 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: close
Cache-Control: no-cache
Location: href=”http://internet-positif.org/site.block?
Upon redirection, the block page shown in Figure 11 was served to users.

The text on the block page reads:
“This forbidden site cannot be accessed because it is indicated that it may contain one of the following: Pornography, Gambling, Phising [sic], SARA [SARA stands for “Suku, Agama, Ras, Antar-golongan,” which refers to content related to ethnicity, religion, race, and intergroup relations], or PROXY. If you feel that this site is not included in any of the aforementioned categories, please contact advankonten [at] depkominfo [dot] go [dot] id.”
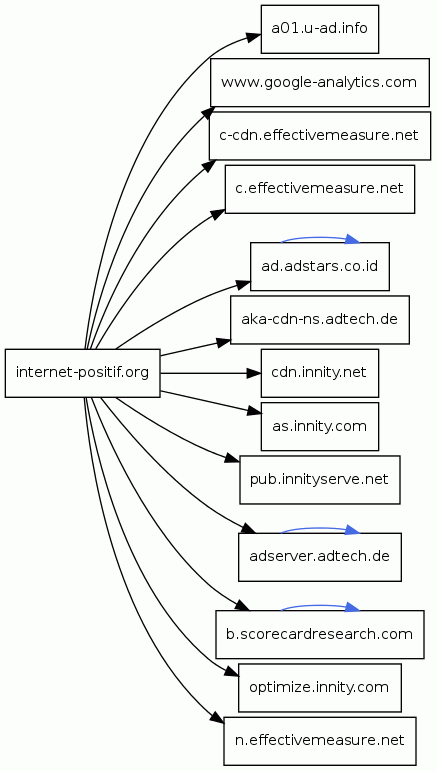
The Trust+ Positif block page serves a number of advertisements hosted on third-party sites. Figure 12 shows the HTTP gets to different domains required when you visit the block page once.
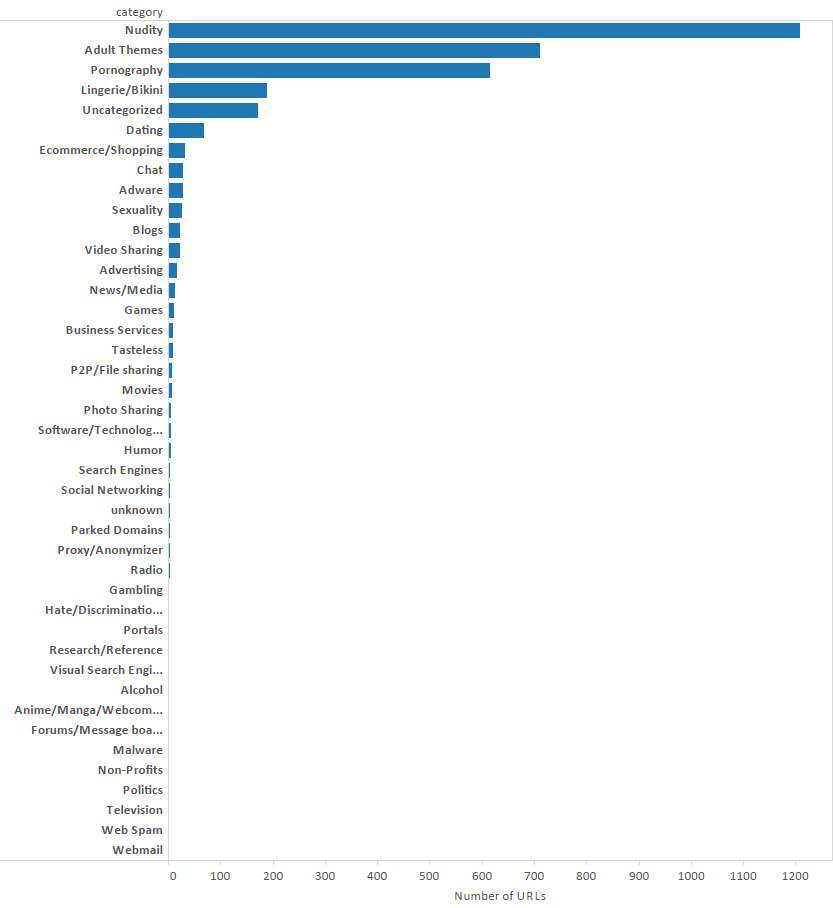
Tests of website accessibility on this network were also undertaken by independent researcher Collin Anderson, who collaborated with us on the research for this post. Anderson performed a DNS consistency test with OONI-probe against the Alexa top 1 million URL list. Based on those results, Anderson extracted the domains that pointed to the filtering server. He then scripted a retrieval of the OpenDNS assessments on every filtered domain and extracted community categorizations for each. The results of these tests can be found here and the distribution of blocked URLs in each primary category can be seen in Figure 13.
During the IGF, the website for Freegate (www.internetfreedom.org), a circumvention tool, was found to be filtered on this network. On 21 October at 4:00 pm, a conference attendee notified network administrators about this blocked website, and by 11:00 pm the site was made accessible. The prompt response by network administrators and the ISP is an example of remediation for potentially erroneous blocking, but also demonstrates an informal ad-hoc process.
ISP: IGF2013@Indosat
AS: INDOSATM2-ID
Netalyzer Results
Testing conducted on SSID: IGF2103@indosat (AS: INDOSATM2-ID) found 164 URLs blocked out of the sample of 1,387 URLs tested. These websites include LGBT content, independent media sites, critical religious content, gambling websites, and pornography. Websites found blocked included Free Speech TV (www.freespeech.org), Equal Marriage for Same-Sex Couples (www.samesexmarriage.ca), and the Indonesian religious site Faith Freedom (indonesia.faithfreedom.org/doc). The full list of URLs blocked on this ISP can be found here.
This ISP filters by DNS tampering, with all filtered domains resolving to the IP 124.81.92.132. After being redirected to this IP, users are served the block page seen in Figure 14.
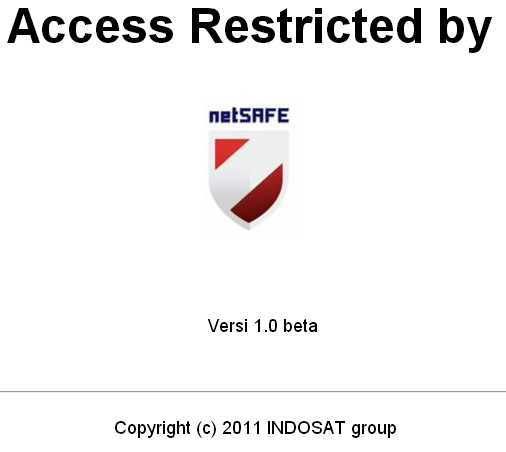
This block page has the following HTML source:
<html>
<body>
<center>
<p>
<hr>
<font face=”arial” size=”15″ color=”black”>
<b>Access Restricted by</b>
<p>
<img src=”logo_netsafe.JPG” alt=”netSAFE”></img>
<p>
<font size=”4″>
Versi 1.0 beta
<hr>
<p>
Copyright (c) 2011 INDOSAT group
</body>
</html>
Cross-ISP Comparison
Indonesia’s highly decentralized filtering environment means that what content is filtered and how filtering is implemented can vary greatly between ISPs. Our results do show such a variation in filtering, although there is a general overlap in the types of content filtered. Our test results show that pornography, a putative focus of the filtering regime, is highly filtered on all ISPs, as is nonpornographic LGBT content. One notable area of difference is anonymizers and circumvention tools, which are heavily filtered on Telkmonet’s IGF network while generally available on the other two networks.
A breakdown of the variation in filtered content between ISPs can be seen in Figure 15.
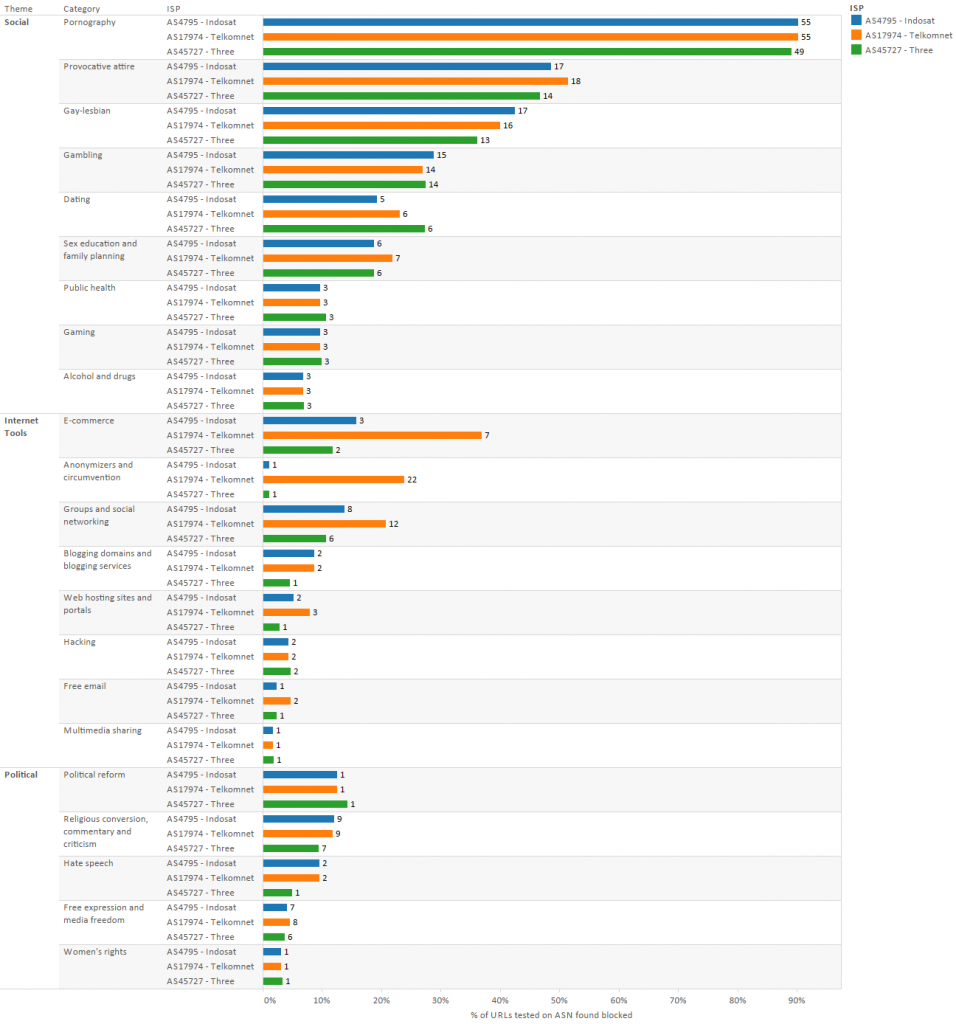
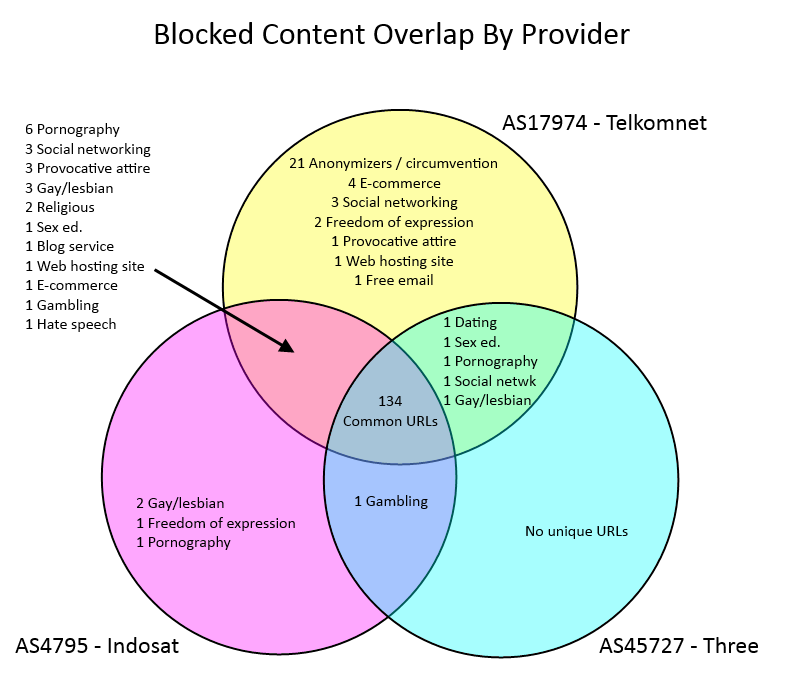
Figure 16 shows the variation and overlap in blocked content between the three ISPs.
Summary and Next Steps
The research and analysis presented here shows that an understanding of content controls requires a combination of methods and insights from both technical and qualitative approaches, and in particular perspectives from those who understand the social, political, cultural, and economic context of Indonesia. It is clear from the data we collected and the analysis we undertook that Indonesian content controls are exercised in a way that is inconsistent, lacks transparency, and includes numerous instances of overblocking, or blocking of content far beyond what is publicly justified and discussed. Some of this overblocking is the consequence of categorization errors; others appear to be the result of overzealous compliance by ISPs; and still others may be the result of other factors, including subtle pressure and influence by government officials or other parties. As Indonesian development in ICTs continues to rapidly progress, the lack of transparency, accountability, and clear processes for content controls will likely exacerbate tensions and disputes in the country among stakeholders operating in an uncertain environment.
Data
Completed lists of URLs used for testing, and URLs found blocked through both remote and client-based tests can be found here:
- CSVs